Exam Details
Exam Code
:412-79Exam Name
:EC-Council Certified Security Analyst (ECSA)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:232 Q&AsLast Updated
:Aug 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 412-79 Questions & Answers
-
Question 221:
You are the security analyst working for a private company out of France. Your current assignment is to obtain credit card information from a Swiss bank owned by that company. After initial reconnaissance, you discover that the bank security defenses are very strong and would take too long to penetrate. You decide to get the information by monitoring the traffic between the bank and one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of FTP packets traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What tool could you use to get this information?
A. RaidSniff
B. Snort
C. Ettercap
D. Airsnort
-
Question 222:
What will the following command accomplish?
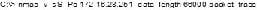
A. Test ability of a router to handle over-sized packets
B. Test the ability of a router to handle fragmented packets
C. Test the ability of a WLAN to handle fragmented packets
D. Test the ability of a router to handle under-sized packets
-
Question 223:
After attending a CEH security seminar, you make a list of changes you would like to perform on your network to increase its security. One of the first things you change is to switch the RestrictAnonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server. Using Userinfo tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
A. RestrictAnonymous must be set to "2" for complete security
B. RestrictAnonymous must be set to "3" for complete security
C. There is no way to always prevent an anonymous null session from establishing
D. RestrictAnonymous must be set to "10" for complete security
-
Question 224:
You are carrying out the last round of testing for your new website before it goes live. The website has many dynamic pages and connects to a SQL backend that accesses your product inventory in a database. You come across a web security site that recommends inputting the following code into a search field on web pages to check for vulnerabilities:
When you type this and click on search, you receive a pop-up window that says:
"This is a test."
What is the result of this test?
A. Your website is vulnerable to web bugs
B. Your website is vulnerable to CSS
C. Your website is not vulnerable
D. Your website is vulnerable to SQL injection
-
Question 225:
How many bits is Source Port Number in TCP Header packet?
A. 48
B. 32
C. 64
D. 16
-
Question 226:
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
A. Windows computers are constantly talking
B. Linux/Unix computers are constantly talking
C. Linux/Unix computers are easier to compromise
D. Windows computers will not respond to idle scans
-
Question 227:
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish here?
A. Enumerate all the users in the domain
B. Perform DNS poisoning
C. Send DOS commands to crash the DNS servers
D. Perform a zone transfer
-
Question 228:
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
A. Windows computers will not respond to idle scans
B. Linux/Unix computers are constantly talking
C. Linux/Unix computers are easier to compromise
D. Windows computers are constantly talking
-
Question 229:
What operating system would respond to the following command?
A. Mac OS X
B. Windows XP
C. Windows 95
D. FreeBSD
-
Question 230:
At what layer of the OSI model do routers function on?
A. 3
B. 4
C. 5
D. 1
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 412-79 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.