Exam Details
Exam Code
:3V0-732Exam Name
:VMware Certified Advanced Professional 7 - Cloud Management and Automation DesignCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:90 Q&AsLast Updated
:Dec 21, 2024
VMware VMware Certifications 3V0-732 Questions & Answers
-
Question 71:
An architect is tasked with designing a multi-region Software Defined Data Center (SDDC) deployment. The operations team has mandated that the solution enable real-time logging for all automation components. The architect makes a design decision to use a vRealize Log Insight cluster in each region, consisting of a total of three nodes. Which three data sources are required to be in scope? (Choose three.)
A. vRealize Automation Appliance
B. NSX Manager, NSX Controller instances and NSX Edge instances
C. vRealize Operations Manager
D. vRealize Orchestrator
E. vRealize IaaS Server
-
Question 72:
IT Services would like to automate the allocation of software applications. The company uses a modern virtual desktop platform with software management capabilities, and the platform supports interoperability via a REST API. The following requirements have been established for this project:
1.
Business users will use a self-service portal to request software added to their existing system.
2.
The requestor may select one or more software applications from a list during the request.
3.
The software application list must be up-to-date.
4.
The virtual desktop team will provide REST API calls needed to interface with the existing platform.
Which three of these listed elements are required for this scenario? (Choose three.)
A. Customization of XaaS form
B. vRealize Orchestrator workflow with script action
C. Resource mapping
D. Resource action
E. External value definition
-
Question 73:
An architect has been tasked with designing a blueprint containing web, application and database machines utilizing NSX for networking. Upon provisioning, network traffic must be automatically restricted to allow:
1.
The web server to communicate only to the application server
2.
The application server to communicate to both the web and database servers
3.
The database server to be blocked from communicating to the other servers
Which two methods could the architect use to accomplish this? (Choose two.)
A. Assign an appropriate security group to the entitled items or entitled service within the entitlement.
B. Add an appropriate security group to the blueprint from within the blueprint properties, under NSX Settings.
C. Create or update an appropriate security group within NSX to include the provisioned machines.
D. Specify an appropriate security group in the blueprint and assign it to each machine.
E. Use an Event Broker subscription to ensure that provisioned machines are receiving the appropriate security group assignment.
-
Question 74:
An architect has been tasked with designing a vRealize Automation blueprint that includes Linux machines.
The design includes a requirement that all newly-created machines be added to the corporate DNS. Which two design specifications will address the needs of this scenario?
A. Use custom properties on each machine within the blueprint that provides the details for adding the machine to the corporate DNS.
B. Create an Event Broker subscription that runs an appropriate vRealize Orchestrator workflow during an appropriate machine lifecycle state.
C. Add and configure the appropriate XaaS component into the machine blueprint.
D. Create an XaaS blueprint that adds the machine to DNS and then builds the machine.
-
Question 75:
Which three statements are true regarding a multitenant deployment where each tenant managed its own infrastructure in vRealize Automation? (Choose three.)
A. Each tenant has an IaaS administrator who could create fabric groups and appoint fabric administrators with their respective tenants.
B. Fabric administrators CANNOT create reservations for business groups in other tenants.
C. Each tenant must provide its own infrastructure resources and CANNOT share a common infrastructure.
D. The system administrator is the only user who logs in to the default tenant to manage system-wide configurations and create tenants.
E. Fabric administrators manage reservations only for the users in their own tenant.
-
Question 76:
Development team members would like to deploy multiple software packages within a blueprint. One of these software packages, Tax Processing 1.0, has licensing requirements. Any member of the finance team can authorize the installation
per request, but the entire team must be notified.
Which approval policies would satisfy this request?
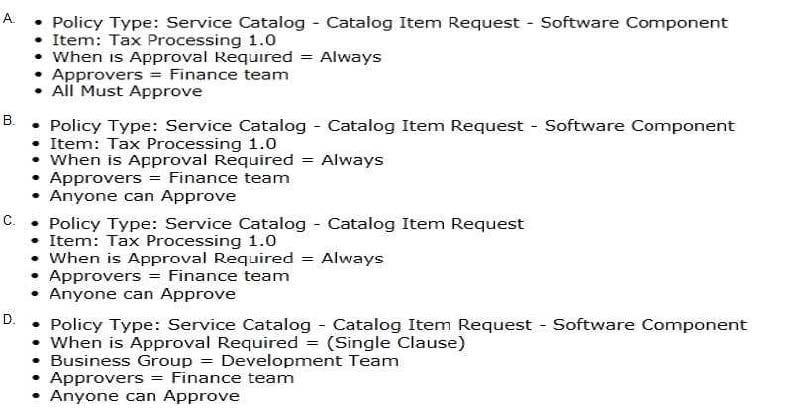
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 77:
An IaaS Administrator has been tasked with organizing virtualization compute resources and cloud endpoints into fabric groups by type and intent. One or more fabric administrators will manage the resources in each fabric group. Which are three considerations to take into account when designing the fabric groups? (Choose three.)
A. Fabric administrators are responsible for creating reservations on the compute resources in their fabric groups to allocate fabric to specific business groups.
B. Fabric administrators monitor the resource use for their group(s) and often are approvers for catalog requests.
C. Fabric administrators may submit requests on behalf of other users. These users could be a member of more than one group and have different roles in different groups.
D. The IaaS administrator must grant the role of fabric administrator to the appropriate users.
E. Fabric groups will be created in a specific tenant, but their resources could be made available to users who belong to business groups in all tenants.
-
Question 78:
A cloud architect is tasked with providing a design for integration with a third-party system.
The following requirements have been identified:
When a user requests a virtual machine, vRealize Automation should pass the user selected application name with its key to the third-party system.
The application list could be updated weekly following the architecture approval meeting. It currently has 250 items.
Impacts to the vRealize Automation virtual machine request screen's performance should be minimized.
What would be the best solution to meet these requirements?
A. Create a vRO action to return application values as "Array\String" by reading from the third-party system dynamically, Create a display drop-down custom property with external values and map it to the vRO action.
B. Design a schedule vRealize Orchestrator (vRO) workflow to read values from the third-party system and store in vRO, Create a vRO action to return application values stored in vRO as "Properties", Create a Display drop-down custom property with external values and map it to the vRO action.
C. Create a Display drop-down custom property with external values and provide AJAX call information to the third-party system.
D. Design a schedule vRO workflow to read values from the third-party and store in vRO, Create a vRO action to return application values stored in vRO as "Array\String", Create a Display drop-down custom property with external values and map it to the vRO action.
-
Question 79:
A company is currently experiencing long infrastructure provisioning times, given that the process to ask,
review, approve and deploy their services is manual with many people involved. It is considering vRealize Automation as a resolution, but it wants to better understand how much resources it is going to need. Which three should the architect
consider when determining the appropriate vRealize Automation deployment size for this environment? (Choose three.)
A. number of managed machines
B. number of concurrent machine provisions
C. number of catalog items
D. number of blueprints
E. number of endpoints
-
Question 80:
A cloud architect is tasked with designing a Guest virtual machine (VM) request form for an organization's new vRealize Automation (vRA) implementation. Its current PowerCLI VM request tool uses a PowerShell script that retrieves user IDs
from Active Directory, which is the same identity source for vRealize Automation. The intent of the script is to retrieve and display John Smith when the actual value in Active Directory is JSmith01.
What is the most secure way to utilize the same script for user's display name in the vRA request form?
A. Design a schedule vRealize Orchestrator workflow to execute the PowerShell Script and update the vRealize Automation drop-down custom property with static values.
B. Design a schedule vRealize Orchestrator (vRO) workflow to execute the PowerShell Script and store values in vRO, then utilize the vRA external drop-down to retrieve these values from vRO.
C. Design a display custom property in the vRA `Administration/Active Directory Policy' that maps to the correct organizational unit.
D. Create a drop-down custom property with external values that returns a display name using the existing PowerShell script.
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-21.20
Professional VMware vSphere 7.x2V0-21.23
VMware vSphere 8.x Professional2V0-31.21
Professional VMware vRealize Automation 8.32V0-31.23
VMware Aria Automation 8.10 Professional
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 3V0-732 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.