Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jun 20, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 871:
If you perform a port scan with a TCP ACK packet, what should an OPEN port return?
A. RST
B. No Reply
C. SYN/ACK
D. FIN
-
Question 872:
Pandora is used to attack __________ network operating systems.
A. Windows
B. UNIX
C. Linux
D. Netware
E. MAC OS
-
Question 873:
Which is the Novell Netware Packet signature level used to sign all packets ?
A. 0
B. 1
C. 2
D. 3
-
Question 874:
One of the better features of NetWare is the use of packet signature that includes cryptographic signatures. The packet signature mechanism has four levels from 0 to 3.
In the list below which of the choices represent the level that forces NetWare to sign all packets?
A. 0 (zero)
B. 1
C. 2
D. 3
-
Question 875:
Which are true statements concerning the BugBear and Pretty Park worms? Select the best answers.
A. Both programs use email to do their work.
B. Pretty Park propagates via network shares and email
C. BugBear propagates via network shares and email
D. Pretty Park tries to connect to an IRC server to send your personal passwords.
E. Pretty Park can terminate anti-virus applications that might be running to bypass them.
-
Question 876:
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe. What caused this?
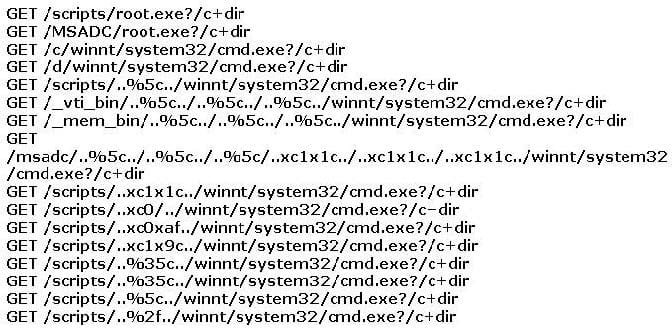
A. The Morris worm
B. The PIF virus
C. Trinoo
D. Nimda E. Code Red
F. Ping of Death
-
Question 877:
Which of the following is one of the key features found in a worm but not seen in a virus?
A. The payload is very small,usually below 800 bytes.
B. It is self replicating without need for user intervention.
C. It does not have the ability to propagate on its own.
D. All of them cannot be detected by virus scanners.
-
Question 878:
The Slammer Worm exploits a stack-based overflow that occurs in a DLL implementing the Resolution Service.
Which of the following Database Server was targeted by the slammer worm?
A. Oracle
B. MSSQL
C. MySQL
D. Sybase
E. DB2
-
Question 879:
Melissa is a virus that attacks Microsoft Windows platforms.
To which category does this virus belong?
A. Polymorphic
B. Boot Sector infector
C. System
D. Macro
-
Question 880:
What is the best means of prevention against viruses?
A. Assign read only permission to all files on your system.
B. Remove any external devices such as floppy and USB connectors.
C. Install a rootkit detection tool.
D. Install and update anti-virus scanner.
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.