Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jun 20, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 841:
While scanning a network you observe that all of the web servers in the DMZ are responding to ACK packets on port 80.
What can you infer from this observation?
A. They are using Windows based web servers.
B. They are using UNIX based web servers.
C. They are not using an intrusion detection system.
D. They are not using a stateful inspection firewall.
-
Question 842:
Carl has successfully compromised a web server from behind a firewall by exploiting a vulnerability in the web server program. He wants to proceed by installing a backdoor program. However, he is aware that not all inbound ports on the firewall are in the open state.
From the list given below, identify the port that is most likely to be open and allowed to reach the server that Carl has just compromised.
A. 53
B. 110
C. 25
D. 69
-
Question 843:
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application.
Which of the following strategies can be used to defeat detection by a network-based IDS application? (Choose the best answer)
A. Create a network tunnel.
B. Create a multiple false positives.
C. Create a SYN flood.
D. Create a ping flood.
-
Question 844:
What makes web application vulnerabilities so aggravating? (Choose two)
A. They can be launched through an authorized port.
B. A firewall will not stop them.
C. They exist only on the Linux platform.
D. They are detectable by most leading antivirus software.
-
Question 845:
Why would an ethical hacker use the technique of firewalking?
A. It is a technique used to discover wireless network on foot.
B. It is a technique used to map routers on a network link.
C. It is a technique used to discover the nature of rules configured on a gateway.
D. It is a technique used to discover interfaces in promiscuous mode.
-
Question 846:
Which one of the following attacks will pass through a network layer intrusion detection system undetected?
A. A teardrop attack
B. A SYN flood attack
C. A DNS spoofing attack
D. A test.cgi attack
-
Question 847:
Once an intruder has gained access to a remote system with a valid username and password, the attacker will attempt to increase his privileges by escalating the used account to one that has increased privileges. such as that of an administrator.
What would be the best countermeasure to protect against escalation of priveges?
A. Give users tokens
B. Give user the least amount of privileges
C. Give users two passwords
D. Give users a strong policy document
-
Question 848:
You are attempting to map out the firewall policy for an organization. You discover your target system is one hop beyond the firewall. Using hping2, you send SYN packets with the exact TTL of the target system starting at port 1 and going up to port 1024.
What is this process known as?
A. Footprinting
B. Firewalking
C. Enumeration
D. Idle scanning
-
Question 849:
Exhibit
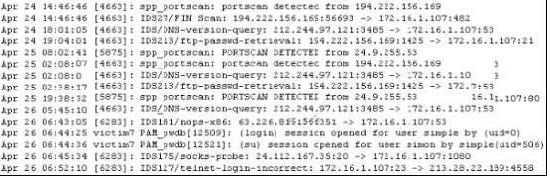
Study the log given in the exhibit,
Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
A. Disallow UDP 53 in from outside to DNS server
B. Allow UDP 53 in from DNS server to outside
C. Disallow TCP 53 in form secondaries or ISP server to DNS server
D. Block all UDP traffic
-
Question 850:
Peter is a Linux network admin. As a knowledgeable security consultant, he turns to you to look for help on a firewall. He wants to use Linux as his firewall and use the latest freely available version that is offered.
What do you recommend? Select the best answer.
A. Ipchains
B. Iptables
C. Checkpoint FW for Linux
D. Ipfwadm
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.