Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jul 25, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 811:
John has a proxy server on his network which caches and filters web access. He shuts down all unnecessary ports and services. Additionally, he has installed a firewall (Cisco PIX) that will not allow users to connect to any outbound ports. Jack, a network user has successfully connected to a remote server on port 80 using netcat. He could in turn drop a shell from the remote machine. Assuming an attacker wants to penetrate John's network, which of the following options is he likely to choose?
A. Use ClosedVPN
B. Use Monkey shell
C. Use reverse shell using FTP protocol
D. Use HTTPTunnel or Stunnel on port 80 and 443
-
Question 812:
Basically, there are two approaches to network intrusion detection: signature detection, and anomaly detection. The signature detection approach utilizes well- known signatures for network traffic to identify potentially malicious traffic. The anomaly detection approach utilizes a previous history of network traffic to search for patterns that are abnormal, which would indicate an intrusion.
How can an attacker disguise his buffer overflow attack signature such that there is a greater probability of his attack going undetected by the IDS?
A. He can use a shellcode that will perform a reverse telnet back to his machine
B. He can use a dynamic return address to overwrite the correct value in the target machine computer memory
C. He can chain NOOP instructions into a NOOP "sled" that advances the processor's instruction pointer to a random place of choice
D. He can use polymorphic shell code-with a tool such as ADMmutate - to change the signature of his exploit as seen by a network IDS
-
Question 813:
Eric notices repeated probes to port 1080. He learns that the protocol being used is designed to allow a host outside of a firewall to connect transparently and securely through the firewall. He wonders if his firewall has been breached.
What would be your inference?
A. Eric network has been penetrated by a firewall breach
B. The attacker is using the ICMP protocol to have a covert channel
C. Eric has a Wingate package providing FTP redirection on his network
D. Somebody is using SOCKS on the network to communicate through the firewall
-
Question 814:
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have complained to Neil that there are a few employees who are visiting offensive web site during work hours, without any consideration for others. Neil knows that he has an up-to-date content filtering system and such access should not be authorized.
What type of technique might be used by these offenders to access the Internet without restriction?
A. They are using UDP that is always authorized at the firewall
B. They are using an older version of Internet Explorer that allow them to bypass the proxy server
C. They have been able to compromise the firewall,modify the rules,and give themselves proper access
D. They are using tunneling software that allows them to communicate with protocols in a way it was not intended
-
Question 815:
Most NIDS systems operate in layer 2 of the OSI model. These systems feed raw traffic into a detection engine and rely on the pattern matching and/or statistical analysis to determine what is malicious. Packets are not processed by the host's TCP/IP stack allowing the NIDS to analyze traffic the host would otherwise discard.
Which of the following tools allows an attacker to intentionally craft packets to confuse pattern-matching NIDS systems, while still being correctly assembled by the host TCP/IP stack to render the attack payload?
A. Defrag
B. Tcpfrag
C. Tcpdump
D. Fragroute
-
Question 816:
During the intelligence gathering phase of a penetration test, you come across a press release by a security products vendor stating that they have signed a multi- million dollar agreement with the company you are targeting. The contract was for vulnerability assessment tools and network based IDS systems. While researching on that particular brand of IDS you notice that its default installation allows it to perform sniffing and attack analysis on one NIC and caters to its management and reporting on another NIC. The sniffing interface is completely unbound from the TCP/IP stack by default. Assuming the defaults were used, how can you detect these sniffing interfaces?
A. Use a ping flood against the IP of the sniffing NIC and look for latency in the responses.
B. Send your attack traffic and look for it to be dropped by the IDS.
C. Set your IP to that of the IDS and look for it as it attempts to knock your computer off the network.
D. The sniffing interface cannot be detected.
-
Question 817:
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address. What can be inferred from this output?
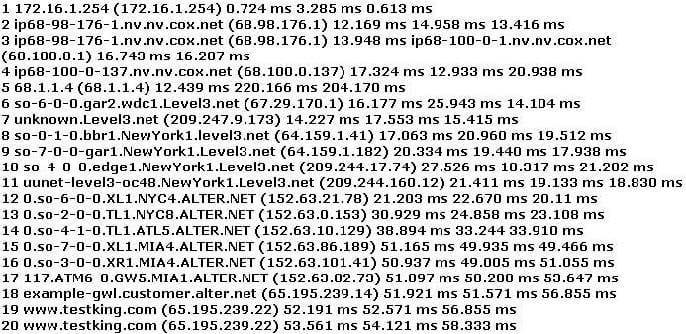
A. An application proxy firewall
B. A stateful inspection firewall
C. A host based IDS
D. A Honeypot
-
Question 818:
What is the tool Firewalk used for?
A. To test the IDS for proper operation
B. To test a firewall for proper operation
C. To determine what rules are in place for a firewall
D. To test the webserver configuration
E. Firewalk is a firewall auto configuration tool
-
Question 819:
What is a primary advantage a hacker gains by using encryption or programs such as Loki?
A. It allows an easy way to gain administrator rights
B. It is effective against Windows computers
C. It slows down the effective response of an IDS
D. IDS systems are unable to decrypt it
E. Traffic will not be modified in transit
-
Question 820:
You perform the above traceroute and notice that hops 19 and 20 both show the same IP address.

This probably indicates what?
A. A host based IDS
B. A Honeypot
C. A stateful inspection firewall
D. An application proxying firewall
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.