Exam Details
Exam Code
:312-50V10Exam Name
:EC-Council Certified Ethical Hacker (C|EH v10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:747 Q&AsLast Updated
:Jul 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V10 Questions & Answers
-
Question 491:
Which of the following processes evaluates the adherence of an organization to its stated security policy?
A. Vulnerability assessment
B. Penetration testing
C. Risk assessment
D. Security auditing
-
Question 492:
Which of the following is a hashing algorithm?
A. MD5
B. PGP
C. DES
D. ROT13
-
Question 493:
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set: The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
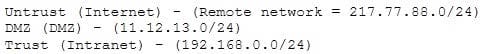
A. Permit 217.77.88.0/24 11.12.13.0/24 RDP 3389
B. Permit 217.77.88.12 11.12.13.50 RDP 3389
C. Permit 217.77.88.12 11.12.13.0/24 RDP 3389
D. Permit 217.77.88.0/24 11.12.13.50 RDP 3389
-
Question 494:
A hacker is attempting to use nslookup to query Domain Name Service (DNS). The hacker uses the nslookup interactive mode for the search. Which command should the hacker type into the command shell to request the appropriate records?
A. Locate type=ns
B. Request type=ns
C. Set type=ns
D. Transfer type=ns
-
Question 495:
Which of the following does proper basic configuration of snort as a network intrusion detection system require?
A. Limit the packets captured to the snort configuration file.
B. Capture every packet on the network segment.
C. Limit the packets captured to a single segment.
D. Limit the packets captured to the /var/log/snort directory.
-
Question 496:
A hacker is attempting to see which ports have been left open on a network. Which NMAP switch would the hacker use?
A. -sO
B. -sP
C. -sS
D. -sU
-
Question 497:
A developer for a company is tasked with creating a program that will allow customers to update their billing and shipping information. The billing address field used is limited to 50 characters. What pseudo code would the developer use to avoid a buffer overflow attack on the billing address field?
A. if (billingAddress = 50) {update field} else exit
B. if (billingAddress != 50) {update field} else exit
C. if (billingAddress >= 50) {update field} else exit
D. if (billingAddress <= 50) {update field} else exit
-
Question 498:
Which of the following programming languages is most vulnerable to buffer overflow attacks?
A. Perl
B. C++
C. Python
D. Java
-
Question 499:
Which type of antenna is used in wireless communication?
A. Omnidirectional
B. Parabolic
C. Uni-directional
D. Bi-directional
-
Question 500:
A hacker was able to sniff packets on a company's wireless network. The following information was discovered:
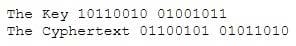
Using the Exlcusive OR, what was the original message?
A. 00101000 11101110
B. 11010111 00010001
C. 00001101 10100100
D. 11110010 01011011
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.