Exam Details
Exam Code
:312-50V10Exam Name
:EC-Council Certified Ethical Hacker (C|EH v10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:747 Q&AsLast Updated
:Jul 06, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V10 Questions & Answers
-
Question 31:
How does a denial-of-service attack work?
A. A hacker prevents a legitimate user (or group of users) from accessing a service
B. A hacker uses every character, word, or letter he or she can think of to defeat authentication
C. A hacker tries to decipher a password by using a system, which subsequently crashes the network
D. A hacker attempts to imitate a legitimate user by confusing a computer or even another person
-
Question 32:
During an Xmas scan what indicates a port is closed?
A. No return response
B. RST
C. ACK
D. SYN
-
Question 33:
What did the following commands determine?
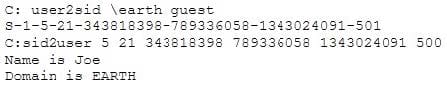
A. That the Joe account has a SID of 500
B. These commands demonstrate that the guest account has NOT been disabled
C. These commands demonstrate that the guest account has been disabled
D. That the true administrator is Joe
E. Issued alone, these commands prove nothing
-
Question 34:
One of your team members has asked you to analyze the following SOA record. What is the version?
Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.) (Choose four.)
A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
-
Question 35:
What does the following command in netcat do?
nc -l -u -p55555 < /etc/passwd
A. logs the incoming connections to /etc/passwd file
B. loads the /etc/passwd file to the UDP port 55555
C. grabs the /etc/passwd file when connected to UDP port 55555
D. deletes the /etc/passwd file when connected to the UDP port 55555
-
Question 36:
Which of the following algorithms can be used to guarantee the integrity of messages being sent, in transit, or stored?
A. symmetric algorithms
B. asymmetric algorithms
C. hashing algorithms
D. integrity algorithms
-
Question 37:
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion detection/prevention tools in your company's network. You have configured the most secure policies and tightened every device on your network. You are confident that hackers will never be able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining access to the network because of presence of "weakest link" in the security chain.
What is Peter Smith talking about?
A. Untrained staff or ignorant computer users who inadvertently become the weakest link in your security chain
B. "zero-day" exploits are the weakest link in the security chain since the IDS will not be able to detect these attacks
C. "Polymorphic viruses" are the weakest link in the security chain since the Anti-Virus scanners will not be able to detect these attacks
D. Continuous Spam e-mails cannot be blocked by your security system since spammers use different techniques to bypass the filters in your gateway
-
Question 38:
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.

Here is a section of the Virus code:
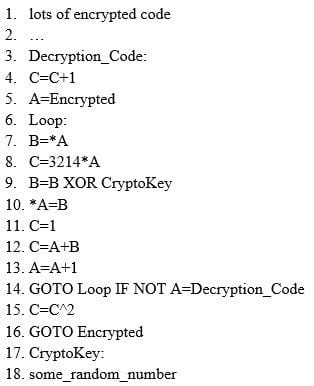
What is this technique called?
A. Polymorphic Virus
B. Metamorphic Virus
C. Dravidic Virus
D. Stealth Virus
-
Question 39:
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
A. There is no way to tell because a hash cannot be reversed
B. The right most portion of the hash is always the same
C. The hash always starts with AB923D
D. The left most portion of the hash is always the same
E. A portion of the hash will be all 0's
-
Question 40:
An attacker runs netcat tool to transfer a secret file between two hosts.

He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the wire?
A. Machine A: netcat -l -p -s password 1234 < testfileMachine B: netcat
B. Machine A: netcat -l -e magickey -p 1234 < testfileMachine B: netcat
C. Machine A: netcat -l -p 1234 < testfile -pw passwordMachine B: netcat
1234 -pw password D. Use cryptcat instead of netcat
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.