Exam Details
Exam Code
:312-49Exam Name
:ECCouncil Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Jul 21, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49 Questions & Answers
-
Question 11:
What does the command "C:\>wevtutil gl
" display? A. Configuration information of a specific Event Log
B. Event logs are saved in .xml format
C. Event log record structure
D. List of available Event Logs
-
Question 12:
Joshua is analyzing an MSSQL database for finding the attack evidence and other details, where should he look for the database logs?
A. Model.log
B. Model.txt
C. Model.ldf
D. Model.lgf
-
Question 13:
What is the name of the first reserved sector in File allocation table?
A. Volume Boot Record
B. Partition Boot Sector
C. Master Boot Record
D. BIOS Parameter Block
-
Question 14:
Which list contains the most recent actions performed by a Windows User?
A. MRU
B. Activity
C. Recents
D. Windows Error Log
-
Question 15:
The given image displays information about date and time of installation of the OS along with service packs, patches, and sub-directories. What command or tool did the investigator use to view this output?
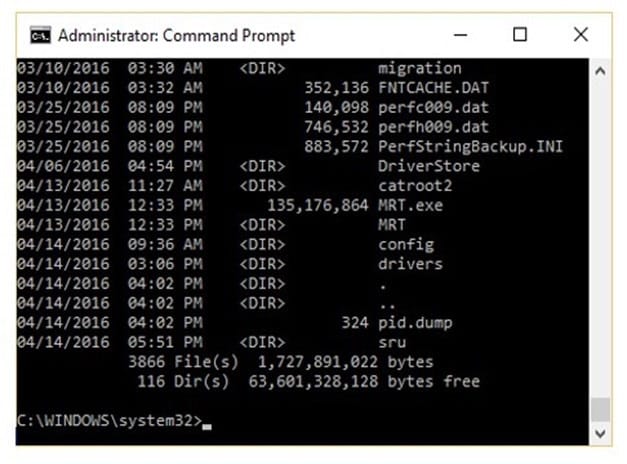
A. dir /o:d
B. dir /o:s
C. dir /o:e
D. dir /o:n
-
Question 16:
Which of the following tools is not a data acquisition hardware tool?
A. UltraKit
B. Atola Insight Forensic
C. F-Response Imager
D. Triage-Responder
-
Question 17:
What is the framework used for application development for iOS-based mobile devices?
A. Cocoa Touch
B. Dalvik
C. Zygote
D. AirPlay
-
Question 18:
Chong-lee, a forensics executive, suspects that a malware is continuously making copies of files and folders on a victim system to consume the available disk space. What type of test would confirm his claim?
A. File fingerprinting
B. Identifying file obfuscation
C. Static analysis
D. Dynamic analysis
-
Question 19:
Which of the following tool is used to locate IP addresses?
A. SmartWhois
B. Deep Log Analyzer
C. Towelroot
D. XRY LOGICAL
-
Question 20:
Which of the following protocols allows non-ASCII files, such as video, graphics, and audio, to be sent through the email messages?
A. MIME
B. BINHEX
C. UT-16
D. UUCODE
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.