Exam Details
Exam Code
:312-39Exam Name
:EC-Council Certified SOC Analyst (CSA)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:100 Q&AsLast Updated
:Aug 06, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-39 Questions & Answers
-
Question 21:
Which of the following stage executed after identifying the required event sources?
A. Identifying the monitoring Requirements
B. Defining Rule for the Use Case
C. Implementing and Testing the Use Case
D. Validating the event source against monitoring requirement
-
Question 22:
Identify the attack in which the attacker exploits a target system through publicly known but still unpatched vulnerabilities.
A. Slow DoS Attack
B. DHCP Starvation
C. Zero-Day Attack
D. DNS Poisoning Attack
-
Question 23:
Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of the company and wanted to check the logs that are generated by access control list numbered 210.
What filter should Peter add to the 'show logging' command to get the required output?
A. show logging | access 210
B. show logging | forward 210
C. show logging | include 210
D. show logging | route 210
-
Question 24:
Which of the following is a correct flow of the stages in an incident handling and response (IHandR) process?
A. Containment
-
Question 25:
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.
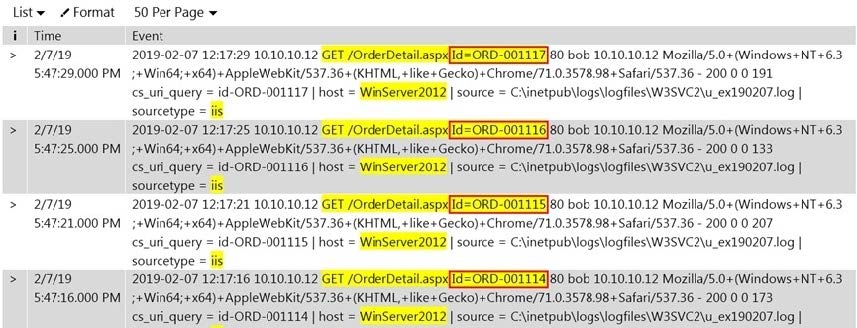
What does this event log indicate?
A. Directory Traversal Attack
B. XSS Attack
C. SQL Injection Attack
D. Parameter Tampering Attack
-
Question 26:
Mike is an incident handler for PNP Infosystems Inc. One day, there was a ticket raised regarding a critical incident and Mike was assigned to handle the incident. During the process of incident handling, at one stage, he has performed incident analysis and validation to check whether the incident is a true incident or a false positive.
Identify the stage in which he is currently in.
A. Post-Incident Activities
B. Incident Recording and Assignment
C. Incident Triage
D. Incident Disclosure
-
Question 27:
Which of the following attack inundates DHCP servers with fake DHCP requests to exhaust all available IP addresses?
A. DHCP Starvation Attacks
B. DHCP Spoofing Attack
C. DHCP Port Stealing
D. DHCP Cache Poisoning
-
Question 28:
What does [-n] in the following checkpoint firewall log syntax represents?
fw log [-f [-t]] [-n] [-l] [-o] [-c action] [-h host] [-s starttime] [-e endtime] [-b starttime endtime] [-u unification_scheme_file] [-m unification_mode(initial|semi|raw)] [-a] [-k (alert name|all)] [-g] [logfile]
A. Speed up the process by not performing IP addresses DNS resolution in the Log files
B. Display both the date and the time for each log record
C. Display account log records only
D. Display detailed log chains (all the log segments a log record consists of)
-
Question 29:
In which phase of Lockheed Martin's
-
Question 30:
Identify the attack, where an attacker tries to discover all the possible information about a target network before launching a further attack.
A. DoS Attack
B. Man-In-Middle Attack
C. Ransomware Attack
D. Reconnaissance Attack
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-39 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.