300-215 Exam Details
-
Exam Code
:300-215 -
Exam Name
:Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR) -
Certification
:CyberOps Professional -
Vendor
:Cisco -
Total Questions
:115 Q&As -
Last Updated
:Jan 11, 2026
Cisco 300-215 Online Questions & Answers
-
Question 1:
What are two features of Cisco Secure Endpoint? (Choose two.)
A. file trajectory
B. rogue wireless detection
C. Orbital Advanced Search
D. web content filtering
E. full disk encryption -
Question 2:
Refer to the exhibit.
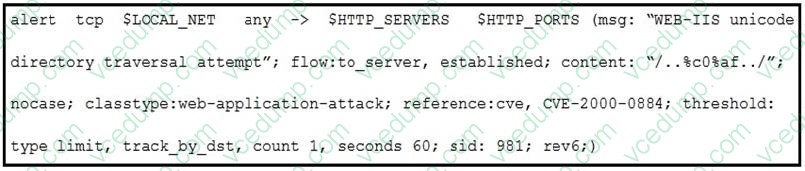
A company that uses only the Unix platform implemented an intrusion detection system. After the initial configuration, the number of alerts is overwhelming, and an engineer needs to analyze and classify the alerts. The highest number of alerts were generated from the signature shown in the exhibit. Which classification should the engineer assign to this event?
A. True Negative alert
B. False Negative alert
C. False Positive alert
D. True Positive alert -
Question 3:
During a routine inspection of system logs, a security analyst notices an entry where Microsoft Word initiated a PowerShell command with encoded arguments. Given that the user's role does not involve scripting or advanced document processing, which action should the analyst take to analyze this output for potential indicators of compromise?
A. Monitor the Microsoft Word startup times to ensure they align with business hours.
B. Confirm that the Microsoft Word license is valid and the application is updated to the latest version.
C. Validate the frequency of PowerShell usage across all hosts to establish a baseline.
D. Review the encoded PowerShell arguments to decode and determine the intent of the script. -
Question 4:
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
A. An engineer should check the list of usernames currently logged in by running the command$ who | cut ?d' ` -f1| sort | uniq
B. An engineer should check the server's processes by running commandsps -auxandsudo ps -a
C. An engineer should check the services on the machine by running the commandservice -status-all
D. An engineer should check the last hundred entries of a web server with the commandsudo tail -100 /var /log/apache2/access.log -
Question 5:
An organization experienced a sophisticated phishing attack that resulted in the compromise of confidential information from thousands of user accounts. The threat actor used a land and expand approach, where initially accessed account was used to spread emails further. The organization's cybersecurity team must conduct an in-depth root cause analysis to uncover the central factor or factors responsible for the success of the phishing attack. The very first victim of the attack was user with email 500236186@test.com. The primary objective is to formulate effective strategies for preventing similar incidents in the future. What should the cybersecurity engineer prioritize in the root cause analysis report to demonstrate the underlying cause of the incident?
A. investigation into the specific vulnerabilities or weaknesses in the organization's email security systems that were exploited by the attackers
B. evaluation of the organization's incident response procedures and the performance of the incident response team
C. examination of the organization's network traffic logs to identify patterns of unusual behavior leading up to the attack
D. comprehensive analysis of the initial user for presence of an insider who gained monetary value by allowing the attack to happen -
Question 6:
An organization recovered from a recent ransomware outbreak that resulted in significant business damage. Leadership requested a report that identifies the problems that triggered the incident and the security team's approach to address these problems to prevent a reoccurrence. Which components of the incident should an engineer analyze first for this report?
A. impact and flow
B. cause and effect
C. risk and RPN
D. motive and factors -
Question 7:
Refer to the exhibit.
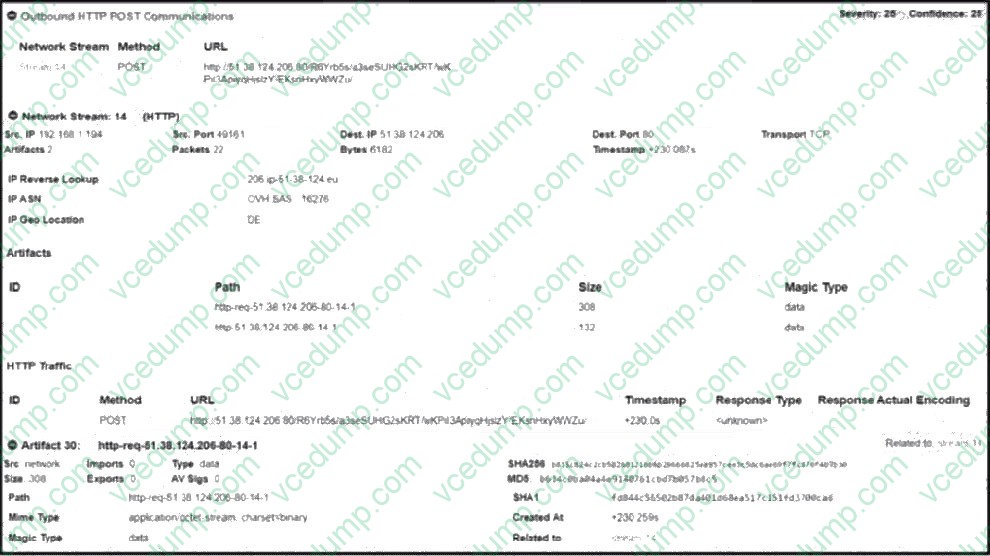
Outbound HTTP POST Communication Summary
Severity: 25
Confidence: 25
Network Stream Information
Source IP: 192.168.1.9
Source Port: 49181
Destination IP: 51.38.124.206
Destination Port: 80 (HTTP)
Protocol: TCP
Packets: 22
Bytes Sent: 6392
Timestamp: +230.08s
POST Request
Method: POST
URL: http://51.38.124.206:80/8RYb5b/a3seSUhG2sKRT/kPKl3ApipvHsi2vYEKsnHkyWWZu/
Mime Type: application/octet-stream; charset=binary
Magic Type: data
Payload Size: 308 bytes
Response Type: unknown
SHA256:8b3cca824e991631c15df937ddf23b5c16f3700c8abcecacb91e03eafd607c3f
MD5:3cbc4ae6c4e9a148761cb1d7857b7eb5
IP Details
Reverse DNS: 206-51-38-124.ovh.net
ASN: OVH SAS (16276)
Geo-Location: Germany (DE)
Threat Insight
Suspicious POST request to a potentially malicious server.
Payload is binary and likely contains malware.
Indicators of Compromise (IOCs):
URL: http://51.38.124.206/...
IP: 51.38.124.206
SHA256 and MD5 hashes
Cisco Secure Malware Analytics identifies outbound HTTP POST communication from an internal host to IP address 51.38.124.206 over port 80. The analysis flags this behavior with severity and confidence scores of 25, and notes that binary
data was sent in 22 packets totaling over 6,000 bytes. What conclusion can be drawn from this observation?
A. Destination IP 51.38.124.206 is identified as malicious
B. MD5 D634c0ba04a4e9140761cbd7b057t>8c5 is identified as malicious
C. Path http-req-51.38.124.206-80-14-1 is benign
D. The stream must be analyzed further via the pcap file -
Question 8:
Refer to the exhibit.
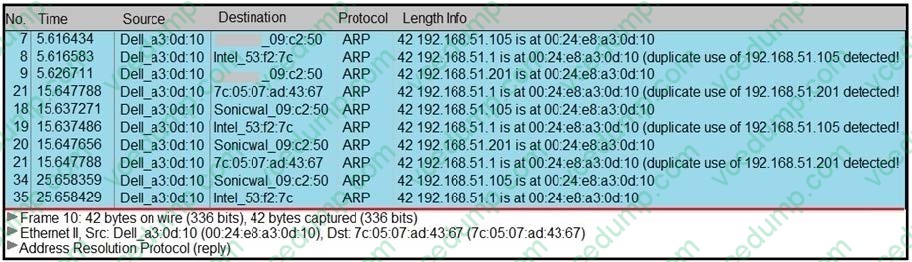
A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A. DNS spoofing; encrypt communication protocols
B. SYN flooding; block malicious packets
C. ARP spoofing; configure port security
D. MAC flooding; assign static entries -
Question 9:
An engineer is analyzing a DoS attack and notices that the perpetrator used a different IP address to hide their system IP address and avoid detection. Which anti-forensics technique did the perpetrator use?
A. cache poisoning
B. spoofing
C. encapsulation
D. onion routing -
Question 10:
Refer to the code.
Dec 28 11:27:10 CyberOps sshd[8423]: Failed password for invalid user admins from Cyber port 44216 ssh2 Dec 28 11:27:13 CyberOps sshd[8425]: Failed password for invalid user phoenix from Cyber port 20532 ssh2 Dec 28 11:27:17 CyberOps sshd[8428]: Failed password for invalid user test from Cyber port 24492 ssh2 Dec 28 11:27:22 CyberOps sshd[8430]: Failed password for invalid user rainbow from Cyber port 46591 ssh2 Dec 28 11:27:25 CyberOps sshd[8432]: Failed password for invalid user runner from Cyber port 57129 ssh2 Dec 28 11:27:34 CyberOps sshd[8434]: Failed password for invalid user user from Cyber port 11960 ssh2 Dec 28 11:27:37 CyberOps sshd[8437]: Failed password for invalid user abc123 from Cyber port 5921 ssh2 Dec 28 11:27:46 CyberOps sshd[8439]: Failed password for invalid user passwd from Cyber port 21238 ssh2
A web hosting company analyst is analyzing the latest traffic because there was a 20% spike in server CPU usage recently. After correlating the logs, the problem seems to be related to the bad actor activities.
Which attack vector is used and what mitigation can the analyst suggest?
A. SQL Injection; implement input validation and use parameterized queries.
B. Distributed denial of service; use rate limiting and DDoS protection services.
C. Phishing attack; conduct regular user training and use email filtering solutions.
D. Brute-force attack; implement account lockout policies and roll out MFA.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-215 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.