Exam Details
Exam Code
:2V0-621Exam Name
:VMware Certified Professional 6 - Data Center VirtualizationCertification
:VMware CertificationsVendor
:VMwareTotal Questions
:246 Q&AsLast Updated
:Dec 19, 2024
VMware VMware Certifications 2V0-621 Questions & Answers
-
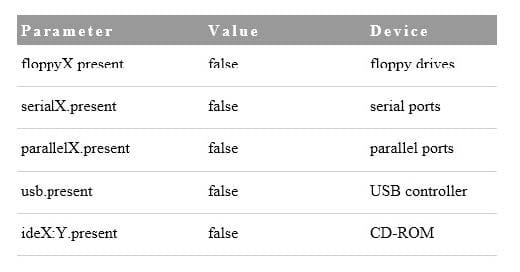
Question 141:
To reduce the attack vectors for a virtual machine, which two settings should an administrator set to false? (Choose two.)
A. keyboard.present
B. vmnicX:Y.present
C. ideX:Y.present
D. serial.present
-
Question 142:
An administrator wants to configure an ESXi 6.x host to use Active Directory (AD) to manage users and groups. The AD domain group ESX Admins was previously created.
Which two conditions should be considered when planning this configuration? (Choose two.)
A. If administrative access for ESX Admins is not desired, an alternate AD group must be used.
B. The users in ESX Admins are granted administrative privileges in vCenter Server.
C. The users in ESX Admins are not restricted by Lockdown Mode.
D. An ESXi host provisioned with Auto Deploy cannot store AD credentials.
-
Question 143:
An administrator has noticed that virtual machine VM2 in the vApp show in the Exhibit is demonstrating poor performance.
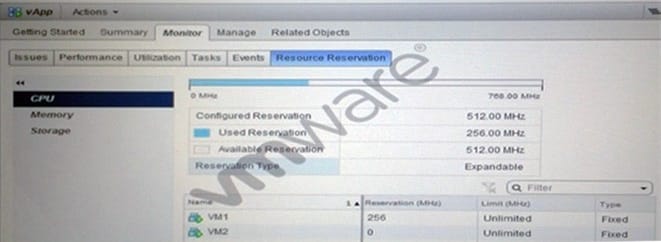
Which three changes, if performed separately, would improve the performance of VM2? (Choose three.)
A. Remove the CPU limit on the vApp.
B. Remove the CPU limit on the resource pool
C. Increase the CPU reservation on virtual machine VM1.
D. Power off virtual machine VM1.
E. Increase the CPU reservation on virtual machine VM2.
-
Question 144:
An administrator is building a large virtual machine that will require as many vCPUs as the host can support. An ESXi 6.x host has these specifications:
1.
Four 24-core Intel Xeon Processors
2.
256 GB of Memory
3.
512 GB Local disk space using VMFS5
What is the maximum number of virtual CPUs that the virtual machine can be allocated?
A. 64
B. 96
C. 128
D. 192
-
Question 145:
An administrator is configuring an identity source for Single Sign-On. The administrator will use the
machine that Single Sign-on is running on, but does not want all users on the machine to be visible to
SSO.
Which identity Source meets this requirement?
A. LocalOS
B. Active Directory as an LDAP service
C. OpenLDAP
D. Active Directory (Integrated Windows Authentication)
-
Question 146:
An administrator has a virtual machine (VM) that uses a shared USB device.
Which option will allow the VM to utilize vMotion while retaining the maximum possible functionality?
A. Disable the USB device from the VM.
B. Remove the device from the VM
C. Configure the VM to support vMotion while the device is connected
D. Enable migration support for the individual USB device's
-
Question 147:
An administrator needs to configure a storage solution for a vSphere 6.x implementation with these characteristics:
1.
Snapshot support
2.
vMotion Capability
3.
Clustering across multiple ESXi hosts
4.
Database application with high transaction count
5.
vFlash Read Cache
Which solution meets all of the stated requirements?
A. A vmdk located on a Shared VMFS datastore
B. A Virtual Mode Raw Device Mapped LUN
C. A Physical Mode Raw Device Mapped LUN
D. A virtual SAN-based vmdk
-
Question 148:
Which two statements are true regarding upgrading from a Distributed vCenter Server 5.x to vCenter Server 6.x? (Choose two.)
A. vCenter Single Sign-On becomes part of the Platform Services Controller
B. The vCenter Server service is not migrated during the upgrade process.
C. The vSphere License Service is migrated to the new vCenter Server 6.x instance.
D. vCenter inventory Service becomes part of the Platform Services Controller
-
Question 149:
Refer to the Exhibit.
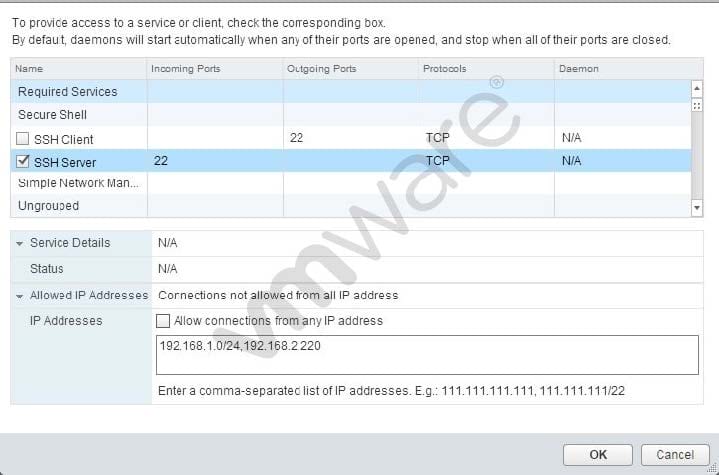
An administrator has configured a firewall rule as shown in the Exhibit. Which statement best describes the ESXi 6.x firewall rule?
A. Connections from the ESXi host to all devices on the 192.168.1.0 network and 192.168.2.220 on port 22 are allowed.
B. Connections coming from IP addresses from the 192.168.1.0 network and 192.168.2.220 on port 22 are allowed.
C. TCP Connections coming from IP addresses from the 192.168.1.0 network and 192.168.2.220 on port 22 are not allowed.
D. TCP Connections from the ESXi host to all devices on the 192.168.1.0 network and 192.168.2.220 on port 22 are not allowed.
-
Question 150:
Refer to the Exhibit.
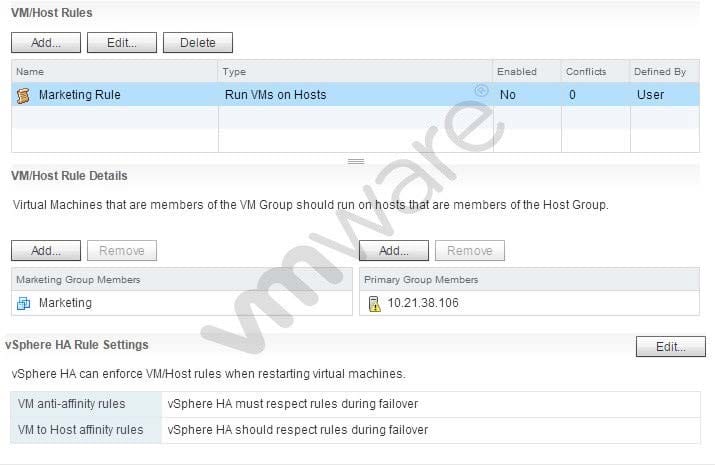
An administrator manages a High Availability (HA)/Distributed Resource Scheduler (DRS)-enabled cluster and has configured the affinity rule shown in the Exhibit.
Which two statements best describe the configuration shown in the exhibit? (Choose two.)
A. HA will not failover Marketing to ESXi hosts that are not in the Host Group.
B. HA will failover Marketing to ESXi hosts that are not in the Host group.
C. DRS will attempt to keep Marketing on the ESXi host 10.21.38.106.
D. DRS will not attempt to keep Marketing on the ESXi host 10.21.28.106.
Related Exams:
1V0-21.20
Associate VMware Data Center Virtualization1V0-31.21
Associate VMware Cloud Management and Automation1V0-41.20
Associate VMware Network Virtualization1V0-61.21
Associate VMware Digital Workspace1V0-71.21
Associate VMware Application Modernization1V0-81.20
Associate VMware Security2V0-11.24
VMware Cloud Foundation 5.2 Administrator2V0-11.25
VMware Cloud Foundation 5.2 Administrator2V0-13.24
VMware Cloud Foundation 5.2 Architect2V0-21.20
Professional VMware vSphere 7.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only VMware exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 2V0-621 exam preparations and VMware certification application, do not hesitate to visit our Vcedump.com to find your solutions here.