Exam Details
Exam Code
:250-441Exam Name
:Administration of Symantec Advanced Threat Protection 3.0Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:95 Q&AsLast Updated
:Aug 10, 2025
Symantec Symantec Certifications 250-441 Questions & Answers
-
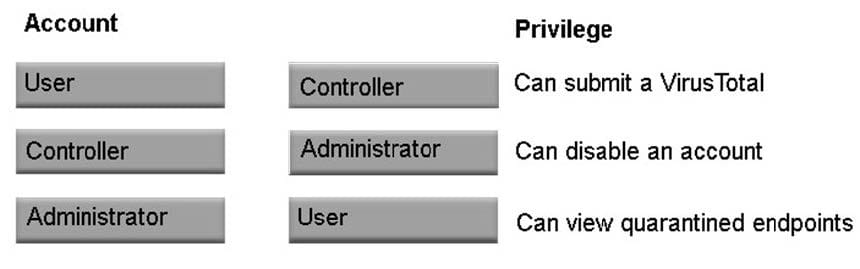
Question 1:
Which level of privilege corresponds to each ATP account type? Match the correct account type to the corresponding privileges.
Select and Place:

-
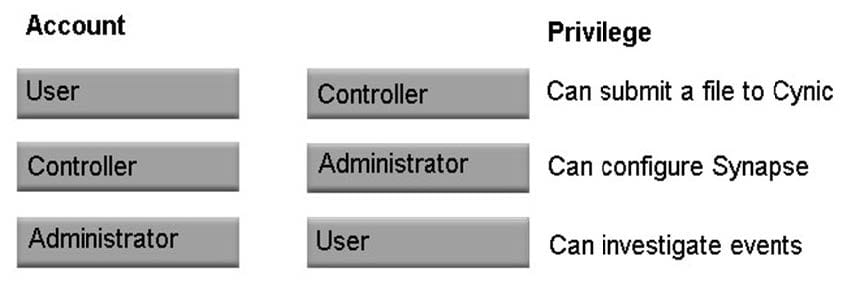
Question 2:
Which level of privilege corresponds to each ATP account type? Match the correct account type to the corresponding privileges.
Select and Place:
-
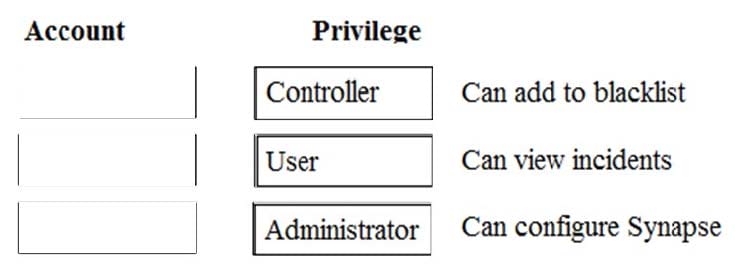
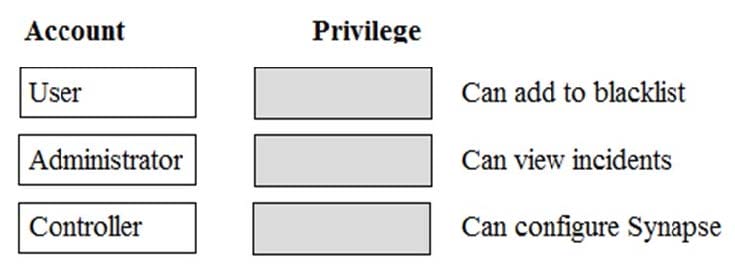
Question 3:
Which level of privilege corresponds to each ATP account type? Match the correct account type to the corresponding privileges.
Select and Place:
-
Question 4:
A network control point discovered a botnet phone-home attempt in the network stream.
Which detection method identified the event?
A. Vantage
B. Insight
C. Antivirus
D. Cynic
-
Question 5:
An organization recently deployed ATP and integrated it with the existing SEP environment. During an
outbreak, the Incident Response team used ATP to isolate several infected endpoints. However, one of the
endpoints could NOT be isolated.
Which SEP protection technology is required in order to use the Isolate and Rejoin features in ATP?
A. Intrusion Prevention
B. Firewall
C. SONAR
D. Application and Device Control
-
Question 6:
A customer has information about a malicious file that has NOT entered the network. The customer wants to know whether ATP is already aware of this threat without having to introduce a copy of the file to the infrastructure.
Which approach allows the customer to meet this need?
A. Use the Cynic portal to check whether the MD5 hash triggers a detection from Cynic
B. Use the ATP console to check whether the SHA-256 hash triggers a detection from Cynic
C. Use the ATP console to check whether the MD5 hash triggers a detection from Cynic
D. Use the Cynic portal to check whether the SHA-256 hash triggers a detection from Cynic
-
Question 7:
An organization has five (5) shops with a few endpoints and a large warehouse where 98% of all computers are located. The shops are connected to the warehouse using leased lines and access internet through the warehouse network.
How should the organization deploy the network scanners to observe all inbound and outbound traffic based on Symantec best practices for Inline mode?
A. Deploy a virtual network scanner at each shop
B. Deploy a virtual network scanner at the warehouse and a virtual network scanner at each shop
C. Deploy a physical network scanner at each shop
D. Deploy a physical network scanner at the warehouse gateway
-
Question 8:
Which policies are required for the quarantine feature of ATP to work?
A. Firewall Policy and Host Integrity Policy
B. Quarantine Policy and Firewall Policy
C. Host Integrity Policy and Quarantine Policy
D. Quarantine and Intrusion Prevention Policy
-
Question 9:
Which access credentials does an ATP Administrator need to set up a deployment of ATP: Endpoint, Network, and Email?
A. Email Security.cloud credentials for email correlation, credentials for the Symantec Endpoint Protection Manager (SEPM) database, and a System Administrator login for the SEPM
B. Active Directory login to the Symantec Endpoint Protection Manager (SEPM) database, and an Email Security.cloud login with full access
C. Symantec Endpoint Protection Manager (SEPM) login and ATP: Email login with service permissions
D. Credentials for the Symantec Endpoint Protection Manager (SEPM) database, and an administrator login for Symantec Messaging Gateway
-
Question 10:
Which two actions an Incident Responder take when downloading files from the ATP file store? (Choose two.)
A. Analyze suspicious code with Cynic
B. Email the files to Symantec Technical Support
C. Double-click to open the files
D. Diagnose the files as a threat based on the file names
E. Submit the files to Security Response
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-441 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.