Exam Details
Exam Code
:250-315Exam Name
:Administration of Symantec Endpoint Protection 12.1Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:275 Q&AsLast Updated
:Jul 06, 2025
Symantec Symantec Certifications 250-315 Questions & Answers
-
Question 61:
A user is unknowingly about to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client's system.
In which feature set order must the threat pass through to successfully infect the system?
A. Download Insight, Firewall, IPS
B. Firewall, IPS, Download Insight
C. IPS, Firewall, Download Insight
D. Download Insight, IPS, Firewall
-
Question 62:
A company has an application that requires network traffic in both directions to multiple systems at a specific external domain. A firewall rule was created to allow traffic to and from the external domain, but the rule is blocking incoming traffic.
What should an administrator enable in the firewall policy to allow this traffic?
A. TCP resequencing
B. Smart DHCP
C. Reverse DNS Lookup
D. Smart WINS
-
Question 63:
A Symantec Endpoint Protection administrator must block traffic from an attacking computer for a specific time period.
Where should the administrator adjust the time to block the attacking computer?
A. in the firewall policy, under Protection and Stealth
B. in the firewall policy, under Built in Rules
C. in the group policy, under External Communication Settings
D. in the group policy, under Communication Settings
-
Question 64:
A threat was detected by Auto-Protect on a client system.
Which command can an administrator run to determine whether additional threats exist?
A. Restart Client Computer
B. Update Content and Scan
C. Enable Network Threat Protection
D. Enable Download Insight
-
Question 65:
In the virus and Spyware Protection policy, an administrator sets the First action to Clean risk and sets If first action fails to Delete risk.
Which two factors should the administrator consider? (Select two.)
A. The deleted file may still be in the Recycle Bin.
B. IT Analytics may keep a copy of the file for investigation.
C. False positives may delete legitimate files.
D. Insight may back up the file before sending it to Symantec.
E. A copy of the threat may still be in the quarantine.
-
Question 66:
Refer to the exhibit.
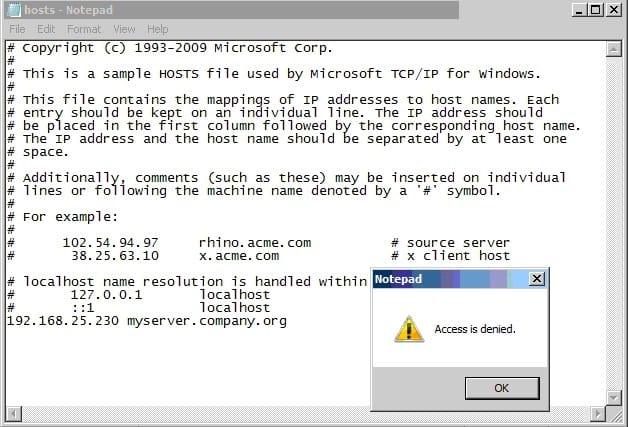
In the use case displayed in the exhibit, why is Notepad unable to save the changes to this file?
A. Tamper Protection is preventing Notepad from modifying the host file.
B. SONAR is set to block host file modifications.
C. System Lockdown is enabled.
D. SONAR High Risk detection is set to Block.
-
Question 67:
An administrator selects the Backup files before attempting to repair the Remediations option in the Auto-Protect policies.
Which two actions occur when a virus is detected? (Select two.)
A. replace the file with a place holder
B. check the reputation
C. store in Quarantine folder
D. send the file to Symantec Insight
E. encrypt the file
-
Question 68:
How are Insight results stored?
A. encrypted on the Symantec Endpoint Protection Manager
B. unencrypted on the Symantec Endpoint Protection Manager
C. encrypted on the Symantec Endpoint Protection client
D. unencrypted on the Symantec Endpoint Protection client
-
Question 69:
Which two options are available when configuring DNS change detected for SONAR? (Select two.)
A. Block
B. Active Response
C. Quarantine
D. Log
E. Trace
-
Question 70:
What are two criteria that Symantec Insight uses to evaluate binary executables? (Select two.)
A. sensitivity
B. prevalence
C. confidentiality
D. content
E. age
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-315 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.