Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 791:
Which two actions in response to traffic sent to a nonlistening UDP port are valid? (Choose two.)
A. ICMP parameter problem
B. UDP packet with the RST flag set
C. ICMP source quench
D. It does not send a reply.
E. ICMP destination unreachable
-
Question 792:
You receive an email at work from your bank that states that your account credentials expire soon. You are given instructions to click a link to update your credentials. Which type of attack is this email?
A. denial of service
B. host-profiling
C. phishing
D. man-in-the-middle
-
Question 793:
You encounter a security alert that traffic with a known TOR exit node has occurred on the network. Which option is the biggest risk?
A. users downloading copyrighted content
B. ransomware communicating after infection
C. data exfiltration
D. user circumvention of the firewall
-
Question 794:
Which two flags set in TCP datagrams are valid ways to close a TCP session? (Choose two.)
A. SYN flag
B. FIN flag
C. RST flag
D. ECT flag
E. PSH flag
-
Question 795:
Which property of a cryptographic hash algorithm is desirable?
A. collision resistance
B. reversibility
C. nondeterminism
D. rainbow tables
-
Question 796:
Which type of data typically consists of connection level, application-specific records generated from network traffic?
A. location data
B. statistical data
C. alert data
D. transaction data
-
Question 797:
What may an increase in IPv4 traffic carrying protocol 41 indicate?
A. additional PPTP traffic due to Windows clients
B. deployment of a GRE network on top of an existing Layer 3 network
C. attempts to tunnel IPv6 traffic through an IPv4 network
D. unauthorized peer-to-peer traffic
-
Question 798:
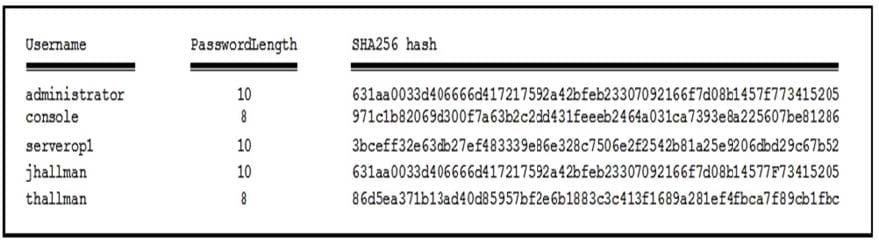
Refer to the exhibit. During an analysis of a password database, this table of usernames and password hashes is found. Which users have the same password?
A. jhallman and thallman
B. administrator and jhallman
C. administrator, console, and jhallman
D. console and thallman
-
Question 799:
Which type of attack affects the availability of the target?
A. SQL injection
B. cross-site scripting
C. social engineering
D. denial of service
-
Question 800:
DNS query uses which protocol
A. TCP
B. UDP
C. HTTP
D. ICMP
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.