Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 531:
What condition does the size of the total addressable virtual memory space depend on?
A. if the Windows version is a server version
B. whether the Windows version is 32-bit or 64-bit
C. the drivers that are loaded with the Windows version
D. the physical size of the hard disk
E. the size of the RAM
-
Question 532:
Malware that can corrupt the virtual memory space of another process can alter the content of which two resources? (Choose two.)
A. another process's content stored in the RAM
B. another process's content stored in the hard disk
C. another process's content stored in the BIOS
D. another process's content stored in the NVRAM
-
Question 533:
When investigating a malicious Windows application, which two Windows components that are associated with the application will also need to be investigated? (Choose two.)
A. threads
B. DLLs
C. processes
D. kernel object handles
-
Question 534:
Which Windows component is used by the applications to modify the system resources?
A. process thread
B. task manager
C. Windows registry
D. object handle
-
Question 535:
When investigating Windows-based security incidents, which can cause the most damage to the integrity of the Windows operating system?
A. malicious Windows drivers that run in kernel mode
B. malicious applications that run in kernel mode
C. malicious applications that run in safe mode
D. malicious rootkits that run in user mode
-
Question 536:
Which type of Windows processes operate within the confines of their own memory space?
A. service
B. EXEC
C. user
D. kernel
E. privileged
-
Question 537:
Malicious Windows operating system codes that share a single virtual address space, and can manage the system CPU and memory resources directly are running in which mode?
A. safe
B. user
C. kernel
D. privileged
-
Question 538:
Which is not a valid Windows operating system version?
A. Windows 10
B. Windows 9
C. Windows 8.1
D. Windows 8
E. Windows 7
F. Windows Server 2012
G. Windows Vista
-
Question 539:
When you are researching a Windows operating system vulnerability (such as CVE-2016-7211), which organization can provide detailed information about the specific vulnerability?
A. Institute of Electrical and Electronics Engineers (IEEE)
B. Control Objectives for Information and Related Technologies (COBIT)
C. National Institute of Standards and Technology (NIST)
D. International Organization for Standardization (ISO)
-
Question 540:
Referring to the nslookup results that is shown below, which two statements are correct? (Choose two.)
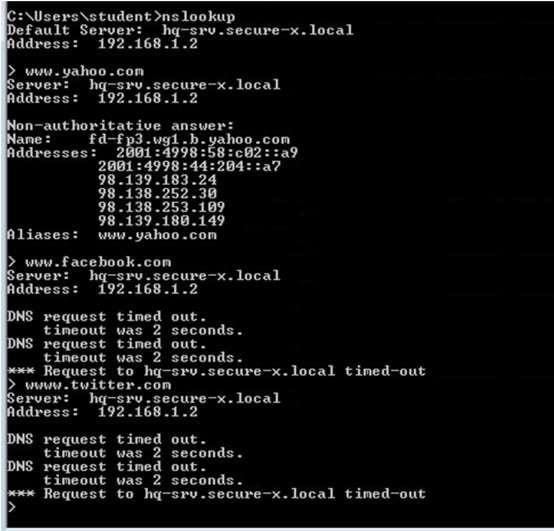
A. 98.139.183.24 is one of the DNS servers.
B. 98.139.180.149 is one of the authoritative DNS servers for www.yahoo.com.
C. 192.168.1.2 is the DNS server IP address.
D. From this host, browsing to www.facebook.com will probably fail.
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.