Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 471:
What are the two primary Linux processes that are used for managing services? (Choose two.)
A. System V init
B. Systemd
C. Task Manager
D. Service Control Manager
-
Question 472:
How would you copy a file that is called evidence from the local system to a Linux host at 192.168.1.33?
A. scp evidence [email protected]:evidence
B. scp [email protected]:evidence evidence
C. ssh evidence [email protected]:evidence
D. ssh [email protected]:evidence evidence
-
Question 473:
If the parent process is terminated before its children, what will the PPID column show in the ps command?
A. N/A
B.
C. 0
D. 1
-
Question 474:
Where is the sda block device stored in the file system?
A. /sys
B. /dev
C. /proc
D. /tmp
-
Question 475:
When a host name is being translated to an IP address, where will the operating system look first?
A. /etc/hosts
B. /etc/hostname
C. /etc/resolv.conf
D. It depends on the configuration of /etc/nsswitch.conf.
-
Question 476:
Given the ls command output that is shown below, what command will permit only the user owner and members of the "staff" group to read or modify the testpcap file?
$ ls -l test -rw-r--r-- 1 jdoe staff 57 Nov 3 10:13 testpcap
A. chmod 660 testpcap
B. chmod 550 testpcap
C. chmod o+rw testpcap
D. chmod staff+rw testpcap
-
Question 477:
A junior analyst is trying to use the tcpdump -i eth1 command on an Ubuntu system, but it is not working. What could be the problem?
A. The tcpdump command requires root level privilege.
B. The tcpdump command requires the Ethernet adapter to be in non-promiscuous mode.
C. The tcpdump command -i option used to specify the interface is an invalid option.
D. The tcpdump command used is missing some of the required options (such as -n and -v).
-
Question 478:
What command would you use to save a packet capture in PCAP format?
A. tcpdump -s 0 -n > evidence.pcap
B. tcpdump -s 0 -n >> evidence.pcap
C. tcpdump -s 0 -n -w evidence.pcap
D. tcpdump -s 0 -n --write evidence.pcap
-
Question 479:
Referring to the output shown below, which two statements are correct? (Choose two.)
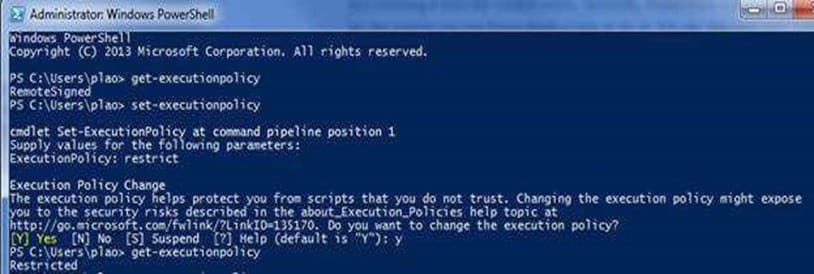
A. Only the externally downloaded PowerShell scripts must be digitally signed.
B. The user changed the PowerShell execution policy to the default setting.
C. PowerShell was run with administrative privileges.
D. There are no restrictions on running PowerShell scripts.
-
Question 480:
What can be used to make a malicious file to appear to have 0 byte size in the dir command output?
A. using AES to encrypt the file
B. using winzip to compress the file
C. using the Master File Table to alter the true file size
D. using NTFS Alternate Data Streams to attach the data to the file
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.