Exam Details
Exam Code
:210-250Exam Name
:Cisco Cybersecurity FundamentalsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:1157 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-250 Questions & Answers
-
Question 241:
Which resource record type is used to display the mail servers for a domain?
A. CNAME
B. MX
C. AAAA
D. PTR
-
Question 242:
DNS listens on which well-known ports?
A. TCP port 53 and UDP port 53
B. UDP port 67 and UDP port 68
C. TCP port 21 and TCP port 22
D. TCP 161 and UDP 161
-
Question 243:
What kind of response message can a root name server send to the DNS recursor to inform it to ask the gTLD name servers for the .com domain name space?
A. referral
B. global
C. ephemeral
D. hierarchal
-
Question 244:
Which three of the following options are uses for the utility nslookup? (Choose three.)
A. query DNS servers for A records
B. display the default DNS server
C. display all mail servers for a domain
D. display owner information about a domain
-
Question 245:
Which statement is correct regarding the web page source code that is shown below?
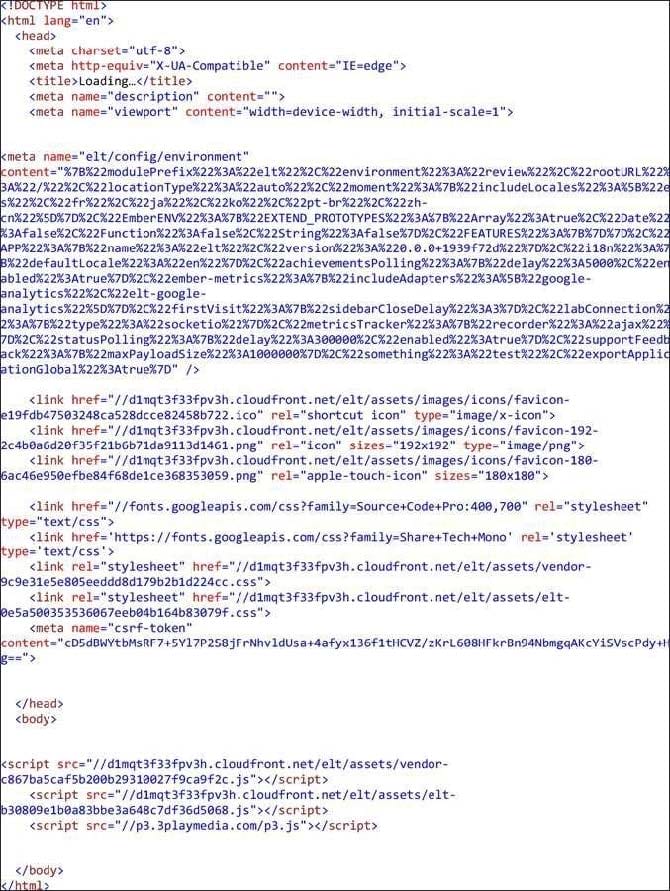
A. The HTML source code references three scripts.
B. The XML source code contains JavaScript.
C. The HTML source code will render a web page that will be both human- and machine-readable.
D. The XML source code is using a cascading style sheet.
-
Question 246:
What best describes the Security Operations Center (SOC)?
A. The SOC is usually responsible for monitoring and maintaining the overall network infrastructure, its primary function is to ensure uninterrupted network service.
B. A SOC is related to the people, processes, and technologies that are involved in providing situational awareness through the detection, containment, and remediation of information security threats.
C. The SOC is responsible for the physical security of a building or installation location.
D. The SOC and NOC are the same entity, with different names. They are responsible for the health and security of the network infrastructure.
-
Question 247:
What are three key components of a threat-centric SOC? (Choose three.)
A. people
B. compliances
C. processes
D. regulations
E. technologies
-
Question 248:
What security management software/process is used to manage employees' mobile devices?
A. MDM
B. SIEM
C. patch management
D. log management
E. configuration management
-
Question 249:
What industry regulation criminalizes production and dissemination of technology, devices, or services that are intended to circumvent digital rights management, or DRM, among other things?
A. PIPEDA
B. HIPPA
C. PCI DSS
D. DMCA
-
Question 250:
What are two goals of compliance regulations? (Choose two.)
A. punish organizations that do not comply
B. reduce an organization's security risk
C. create worldwide standards for all organizations to follow
D. protect the interests of an organization's clients
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-250 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.