Exam Details
Exam Code
:156-915.77Exam Name
:Check Point Certified Security Expert UpdateCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:233 Q&AsLast Updated
:Jun 28, 2025
CheckPoint Checkpoint Certifications 156-915.77 Questions & Answers
-
Question 161:
Your users are defined in a Windows 2008 R2 Active Directory server. You must add LDAP users to a Client Authentication rule. Which kind of user group do you need in the Client Authentication rule in R77?
A. External-user group
B. LDAP group
C. A group with a generic user
D. All Users
-
Question 162:
Study the Rule base and Client Authentication Action properties screen
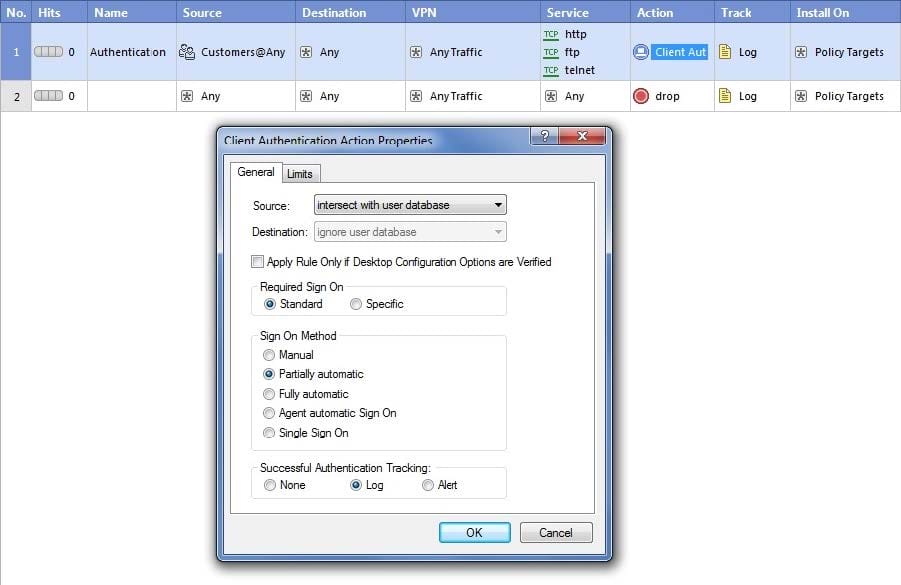
After being authenticated by the Security Gateway, when a user starts an HTTP connection to a Web site, the user tries to FTP to another site using the command line. What happens to the user? The:
A. user is prompted for authentication by the Security Gateway again.
B. FTP data connection is dropped after the user is authenticated successfully.
C. user is prompted to authenticate from that FTP site only, and does not need to enter his username and password for Client Authentication.
D. FTP connection is dropped by Rule 2.
-
Question 163:
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?
A. A group with generic user
B. All users
C. LDAP Account Unit Group
D. Internal user Group
-
Question 164:
The technical-support department has a requirement to access an intranet server. When configuring a User Authentication rule to achieve this, which of the following should you remember?
A. You can only use the rule for Telnet, FTP, SMTP, and rlogin services.
B. The Security Gateway first checks if there is any rule that does not require authentication for this type of connection before invoking the Authentication Security Server.
C. Once a user is first authenticated, the user will not be prompted for authentication again until logging out.
D. You can limit the authentication attempts in the User Properties' Authentication tab.
-
Question 165:
Which of the following are authentication methods that Security Gateway R77 uses to validate connection attempts? Select the response below that includes the MOST complete list of valid authentication methods.
A. Proxied, User, Dynamic, Session
B. Connection, User, Client
C. User, Client, Session
D. User, Proxied, Session
-
Question 166:
In the Rule Base displayed, user authentication in Rule 4 is configured as fully automatic. Eric is a member of the LDAP group, MSD_Group.
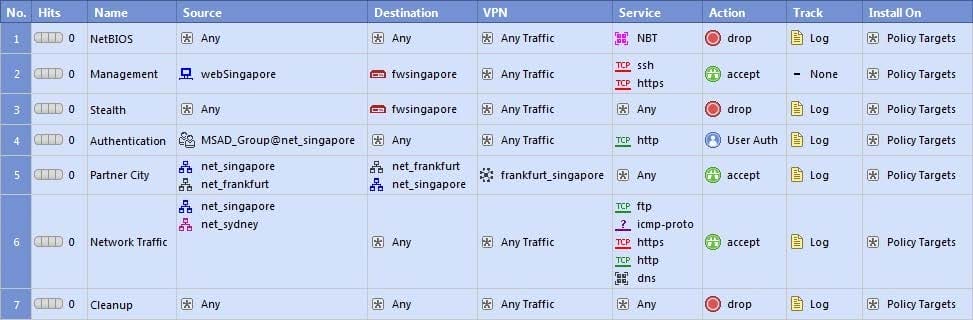
What happens when Eric tries to connect to a server on the Internet?
A. None of these things will happen.
B. Eric will be authenticated and get access to the requested server.
C. Eric will be blocked because LDAP is not allowed in the Rule Base.
D. Eric will be dropped by the Stealth Rule.
-
Question 167:
You cannot use SmartDashboard's User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
A. 1, 2, and 3
B. 2 and 3
C. 1 and 2
D. 1 and 3
-
Question 168:
Which Security Gateway R77 configuration setting forces the Client Authentication authorization time-out to refresh, each time a new user is authenticated? The:
A. Time properties, adjusted on the user objects for each user, in the Client Authentication rule Source.
B. IPS > Application Intelligence > Client Authentication > Refresh User Timeout option enabled.
C. Refreshable Timeout setting, in Client Authentication Action Properties > Limits.
D. Global Properties > Authentication parameters, adjusted to allow for Regular Client Refreshment.
-
Question 169:
Your main internal network 10.10.10.0/24 allows all traffic to the Internet using Hide NAT. You also have a small network 10.10.20.0/24 behind the internal router. You want to configure the kernel to translate the source address only when network 10.10.20.0 tries to access the Internet for HTTP, SMTP, and FTP services. Which of the following configurations will allow this network to access the Internet?
A. Configure three Manual Static NAT rules for network 10.10.20.0/24, one for each service.
B. Configure Automatic Static NAT on network 10.10.20.0/24.
C. Configure one Manual Hide NAT rule for HTTP, FTP, and SMTP services for network 10.10.20.0/24.
D. Configure Automatic Hide NAT on network 10.10.20.0/24 and then edit the Service column in the NAT Rule Base on the automatic rule.
-
Question 170:
You have created a Rule Base for firewall, websydney. Now you are going to create a new policy package with security and address translation rules for a second Gateway.
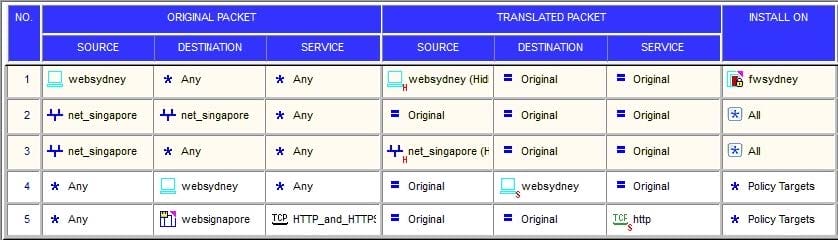
What is TRUE about the new package's NAT rules?
A. Rules 1, 2, 3 will appear in the new package.
B. Only rule 1 will appear in the new package.
C. NAT rules will be empty in the new package.
D. Rules 4 and 5 will appear in the new package.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-915.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.