Exam Details
Exam Code
:156-315.81Exam Name
:Check Point Certified Security Expert - R81 (CCSE)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:624 Q&AsLast Updated
:Jun 05, 2025
CheckPoint Checkpoint Certifications 156-315.81 Questions & Answers
-
Question 491:
Which components allow you to reset a VPN tunnel?
A. vpn tu command or SmartView monitor
B. delete vpn ike sa or vpn she11 command
C. vpn tunnelutil or delete vpn ike sa command
D. SmartView monitor only
-
Question 492:
What is a possible command to delete all of the SSH connections of a gateway?
A. fw sam -I dport 22
B. fw ctl conntab -x -dpott=22
C. fw tab -t connections -x -e 00000016
D. fwaccel dos config set dport ssh
-
Question 493:
When performing a minimal effort upgrade, what will happen to the network traffic?
A. All connections that were initiated before the upgrade will be dropped, causing network downtime
B. All connections that were initiated before the upgrade will be handled normally
C. All connections that were initiated before the upgrade will be handled by the standby gateway
D. All connections that were initiated before the upgrade will be handled by the active gateway
-
Question 494:
Which of the following is NOT a component of a Distinguished Name?
A. Common Name
B. Country
C. User container
D. Organizational Unit
-
Question 495:
Fill in the blanks: Gaia can be configured using the ______ or _____ .
A. GaiaUI; command line interface
B. WebUI; Gaia Interface
C. Command line interface; WebUI
D. Gaia Interface; GaiaUI
-
Question 496:
What is false regarding prerequisites for the Central Deployment usage?
A. The administrator must have write permission on SmartUpdate
B. Security Gateway must have the latest CPUSE Deployment Agent
C. No need to establish SIC between gateways and the management server, since the CDT tool will take care about SIC automatically.
D. The Security Gateway must have a policy installed
-
Question 497:
What are the correct sleps upgrading a HA cluster (Ml is active. M2 is passive) using Multi- Version Cluster(MVC) Upgrade?
A. 1) Enable the MVC mechanism on both cluster members phaprob mvc on 2) Upgrade the passive node M2 to R81.20 3) In SmartConsole. change the version of the cluster object 4) Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails 5) After examine the cluster states upgrade node M1 to R81.20 6) On each Cluster Member, disable the MVC mechanism
B. 1) Enable the MVC mechanism on both cluster members #cphaprob mvc on 2) Upgrade the passive node M2 to R81.20 3) In SmartConsole. change the version of the cluster object
4) Install the Access Control Policy
5) After examine the cluster states upgrade node M1 to R81.20
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy
C. 1) In SmartConsole. change the version of the cluster object 2) Upgrade the passive node M2 to R81.20 3) Enable the MVC mechanism on the upgraded R81.20 Cluster Member M2 Wcphaconf mvc on 4) Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails 5) After examine the cluster states upgrade node M1 to R81.20 6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy SmartConsole. change the version of the cluster object
D. 1) Upgrade the passive node M2 to R81.20 2) Enable the MVC mechanism on the upgraded R81.20 Cluster Member M2 ttcphaconf mvc on 3) In SmartConsole, change the version of the cluster object 4} Install the Access Control Policy 5) After examine the cluster states upgrade node M1 to R81.20 6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy upgrade the passive node M2 to R81.20
-
Question 498:
In the R81 SmartConsole, on which tab are Permissions and Administrators defined?
A. Security Policies
B. Logs and Monitor
C. Manage and Settings
D. Gateways and Servers
-
Question 499:
On the following picture an administrator configures Identity Awareness:
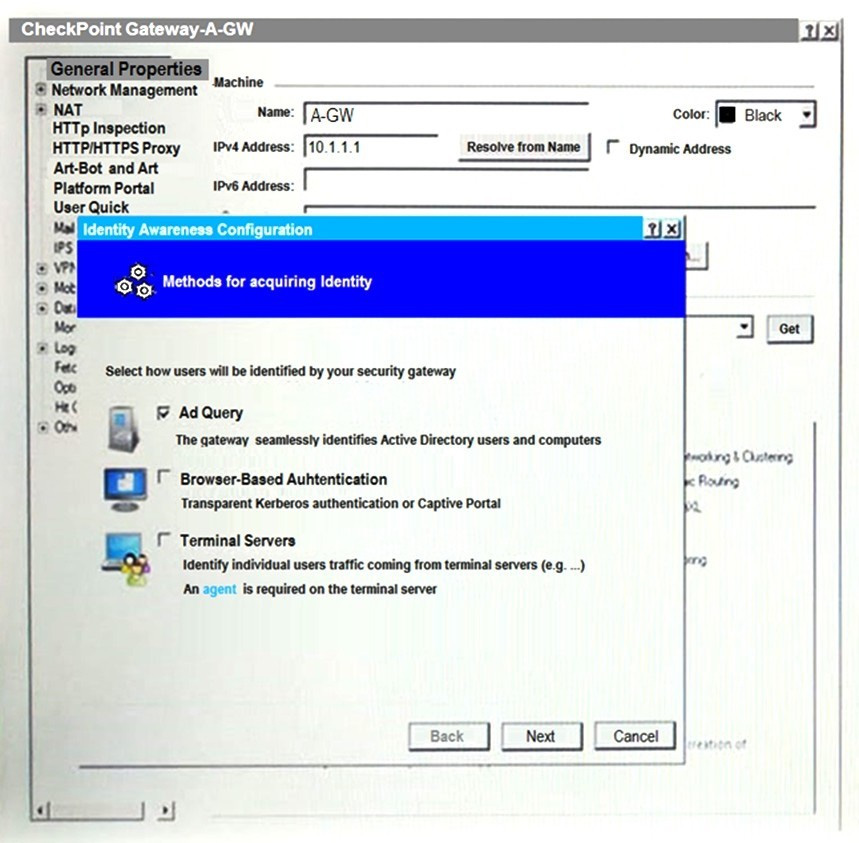
After clicking "Next" the above configuration is supported by:
A. Kerberos SSO which will be working for Active Directory integration
B. Based on Active Directory integration which allows the Security Gateway to correlate Active Directory users and machines to IP addresses in a method that is completely transparent to the user.
C. Obligatory usage of Captive Portal.
D. The ports 443 or 80 what will be used by Browser-Based and configured Authentication.
-
Question 500:
Return oriented programming (ROP) exploits are detected by which security blade?
A. Data Loss Prevention
B. Check Point Anti-Virus / Threat Emulation
C. Application control
D. Intrusion Prevention Software
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.