Exam Details
Exam Code
:156-315.81Exam Name
:Check Point Certified Security Expert - R81 (CCSE)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:624 Q&AsLast Updated
:May 28, 2025
CheckPoint Checkpoint Certifications 156-315.81 Questions & Answers
-
Question 321:
Check Point ClusterXL Active/Active deployment is used when:
A. Only when there is Multicast solution set up.
B. There is Load Sharing solution set up.
C. Only when there is Unicast solution set up.
D. There is High Availability solution set up.
-
Question 322:
The WebUI offers several methods for downloading hotfixes via CPUSE except:
A. Automatic
B. Force override
C. Manually
D. Scheduled
-
Question 323:
Mobile Access Gateway can be configured as a reverse proxy for Internal Web Applications Reverse proxy users browse to a URL that is resolved to the Security Gateway IP address. Which of the following Check Point command is true for enabling the Reverse Proxy:
A. ReverseCLIProxy
B. ReverseProxyCLI
C. ReverseProxy
D. ProxyReverseCLI
-
Question 324:
Why would an administrator see the message below?
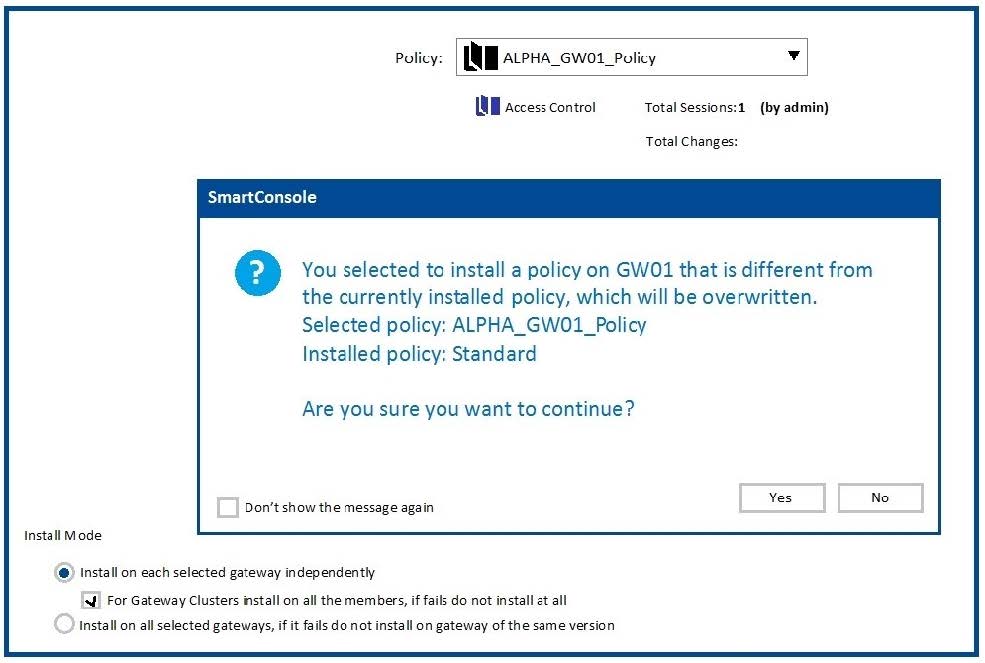
A. A new Policy Package created on both the Management and Gateway will be deleted and must be backed up first before proceeding.
B. A new Policy Package created on the Management is going to be installed to the existing Gateway.
C. A new Policy Package created on the Gateway is going to be installed on the existing Management.
D. A new Policy Package created on the Gateway and transferred to the Management will be overwritten by the Policy Package currently on the Gateway but can be restored from a periodic backup on the Gateway.
-
Question 325:
Which is the command to identify the NIC driver before considering about the employment of the Multi-Queue feature?
A. show interface eth0 mq
B. ethtool A eth0
C. ifconfig -i eth0 verbose
D. ip show Int eth0
-
Question 326:
You need to change the MAC-address on eth2 interface of the gateway. What is the correct way to change MAC-address in Check Point Gaia?
A. In CLISH run: set interface eth2 mac-addr 11:11:11:11:11:11
B. In expert-mode run ifconfig eth1 hw 11:11:11:11 11 11
C. In CLISH run set interface eth2 hw-addr 11 11 11:11:11 11
D. In expert-mode run: ethtool -4 eth2 mac 11 11:11:11:11:11
-
Question 327:
Which firewall daemon is responsible for the FW CLI commands?
A. fwd
B. fwm
C. cpm
D. cpd
-
Question 328:
Which command will reset the kernel debug options to default settings?
A. fw ctl dbg -a 0
B. fw ctl dbg resetall
C. fw ctl debug 0
D. fw ctl debug set 0
-
Question 329:
Bob is asked by Alice to disable the SecureXL mechanism temporary tor further diagnostic by their Check Point partner. Which of the following Check Point Command is true:
A. fwaccel suspend
B. fwaccel standby
C. fwaccel off
D. fwaccel templates
-
Question 330:
The "Hit count" feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits if the Track option is set to "None"?
A. No, it will work independently. Hit Count will be shown only for rules Track option set as Log or alert.
B. Yes it will work independently as long as "analyze all rules" tick box is enabled on the Security Gateway.
C. No, it will not work independently because hit count requires all rules to be logged.
D. Yes it will work independently because when you enable Hit Count, the SMS collects the data from supported Security Gateways.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.