Exam Details
Exam Code
:156-315.77Exam Name
:Check Point Certified Security ExpertCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-315.77 Questions & Answers
-
Question 411:
Your company has the requirement thatSmart Eventreports should show a detailed and accurate view of network activity but also performance should be guaranteed.
Which actions should be taken to achieve that?
(i)
Use same hard driver for database directory, log files and temporary directory
(ii)
Use Consolidation Rules
(iii) Limit logging to blocked traffic only
(iv)
Using Multiple Database Tables
A.
(i) and (ii)
B.
(ii) and (iv)
C.
(i), (ii) and (iv)
D.
(i), (iii) and (iv)
-
Question 412:
Based on the following information, which of the statements below is TRUE?
A DLP Rule Base has the following conditions:
Data Type = Large file (> 500KB)
Source = My Organization
Destination = Free Web Mails
Protocol = Any
Action = Ask User
All other rules are set to Detect.User Checkis enabled and installed on all client machines.
A. When a user uploads a 600 KB file to his Yahoo account via Web Mail (via his browser), he will be prompted byUser Check
B. When a user sends an e-mail with a small body and 5 attachments, each of 200 KB to, he will be prompted byUser Check.
C. When a user sends an e-mail with an attachment larger than 500 KB to, he will be prompted byUser Check.
D. When a user sends an e-mail with an attachment larger than 500KB to, he will be prompted byUser Check.
-
Question 413:
To help organize events,Smart Reporteruses filtered queries. Which of the following is NOT anSmart Eventeventproperty you can query?
A. Event: Critical, Suspect, False Alarm
B. Time:Last Hour, Last Day, Last Week
C. State:Open, Closed, False Alarm
D. Type:Scans, Denial of Service, Unauthorized Entry
-
Question 414:
What is a task of theSmart EventCorrelation Unit?
A. Add events to the events database.
B. Look for patterns according to the installed Event Policy.
C. Assign a severity level to an event
D. Display the received events.
-
Question 415:
Exhibit:
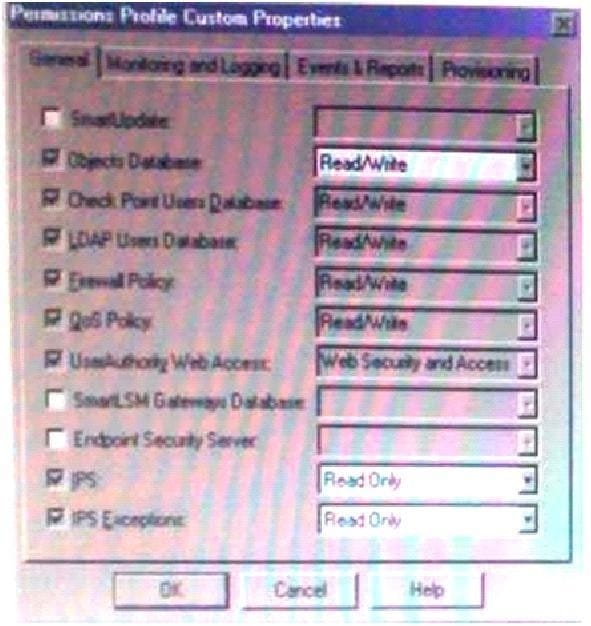
UserA is able to create a SmartLSM Security Cluster Profile , you must select the correct justification.
A. False. The user must have at least Read permissions for the SmartLSM Gateways Database
B. True Only Object Database Read/Write permissions are required to create SmartLSM Profiles
C. False The user must have Read/Write permissions for the SmartLSM Gateways Database.
D. Not enough information to determine. You must know the user's Provisioning permissions to determine whether they are able to create a SmartLSM Security Cluster Profile
-
Question 416:
SmartWorkflow has been enabled with the following configuration:
If a security administrator opens a new session and after making changes to policy, submits the session for approval will be displayed as:
A. Approved
B. In progress
C. Not Approved
D. Awaiting Approval
-
Question 417:
Which Protection Mode does not exist in IPS?
A. Allow
B. Detect
C. Prevent
D. Inactive
-
Question 418:
You set up a mesh VPN Community, so your internal networks can access your partner's network, and vice versa. Your Security Policy encrypts only FTP and HTTP traffic through a VPN tunnel. All other traffic among your internal and
partner networks is sent in clear text.
How do you configure the VPN Community?
A. Disable "accept all encrypted traffic", and put FTP and HTTP in the Excluded services in the Community object. Add a rule in the Security Policy for services FTP and http, with the Community object in the VPN field.
B. Disable "accept all encrypted traffic" in the Community, and add FTP and HTTP services to the Security Policy, with that Community object in the VPN field.
C. Enable "accept all encrypted traffic", but put FTP and HTTP in the Excluded services in the Community. Add a rule in the Security Policy, with services FTP and http, and the Community object in the VPN field.
D. Put FTP and HTTP in the Excluded services in the Community object. Then add a rule in the Security Policy to allow Any as the service, with the Community object in the VPN field.
-
Question 419:
Provisioning Profiles can NOT be applied to:
A. UTM-1 EDGE Appliances
B. UTM-1 Appliances
C. IP Appliances
D. Power-1 Appliances
-
Question 420:
Which of the following actions is most likely to improve the performance of Check Point QoS?
A. Put the most frequently used rules at the bottom of the QoS Rule Base.
B. Define Check Point QoS only on the external interfaces of the QoS Module.
C. Turn per rule limits into per connection limits
D. Turn per rule guarantees into per connection guarantees.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.