Exam Details
Exam Code
:156-315.77Exam Name
:Check Point Certified Security ExpertCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-315.77 Questions & Answers
-
Question 361:
Wayne configures an HTTP Security Server to work with the content vectoring protocol to screen forbidden sites. He has created a URI resource object using CVP with the following settings:
Use CVP
Allow CVP server to modify content
Return data after content is approved
He adds two rules to his Rule Base: one to inspect HTTP traffic going to known forbidden sites, the other to allow all other HTTP traffic.
Wayne sees HTTP traffic going to those problematic sites is not prohibited.
What could cause this behavior?
A. The Security Server Rule is after the general HTTP Accept Rule.
B. The Security Server is not communicating with the CVP server.
C. The Security Server is not configured correctly.
D. The Security Server is communicating with the CVP server, but no restriction is defined in the CVP server.
-
Question 362:
Which Name Resolution protocols are supported in SSL VPN?
A. DNS, hosts, Imhosts, WINS
B. DNS, hosts, Imhosts
C. DNS, hosts, WINS
D. DNS, hosts
-
Question 363:
In Company XYZ, the DLP Administrator defined a new Keywords Data Type that contains a list of secret project names; i.e., Ayalon, Yarkon, Yarden. The threshold is set to At least 2 keywords or phrases. Based on this information, which of the following scenarios will be a match to the Rule Base?
A. A PDF file that contains the following text Yarkon1 can be the code name for the new product. Yardens list of protected sites
B. An MS Excel file that contains the following text Mort resources for Yarkon project.. Are you certain this is about Yarden?
C. A word file that contains the following text will match: Ayalon ayalon AYALON
D. A password protected MS Excel file that contains the following text Ayalon Yarkon Yarden
-
Question 364:
How can you prevent delay-sensitive applications, such as video and voice traffic, from being dropped due to long queue using Check Point QoS solution?
A. Weighted Fair queuing
B. guaranteed per connection
C. Low latency class
D. guaranteed per VoIP rule
-
Question 365:
John is the MegaCorp Security Administrator, and is using Check Point R71. Malcolm is the Security Administrator of a partner company and is using a different vendor's product and both have to build a VPN tunnel between their companies. Both are using clusters with Load Sharing for their firewalls and John is using ClusterXL as a Check Point clustering solution. While trying to establish the VPN, they are constantly noticing problems and the tunnel is not stable and then Malcolm notices that there seems to be 2 SPIs with the same IP from the Check Point site. How can they solve this problem and stabilize the tunnel?
A. This can be solved by running the command Sticky VPN on the Check Point CLI. This keeps the VPN Sticky to one member and the problem is resolved.
B. This is surely a problem in the ISPs network and not related to the VPN configuration.
C. This can be solved when using clusters; they have to use single firewalls.
D. This can easily be solved by using the Sticky decision function in ClusterXL.
-
Question 366:
Laura notices the Microsoft Visual Basic Bits Protection is set to inactive. She wants to set the Microsoft Visual Basic Kill Bits Protection and all other Low Performance Impact Protections to Prevent. She asks her manager for approval and stated she can turn theses on. But he wants Laura to make sure no high Performance Impacted Protections are turned on while changing this setting.
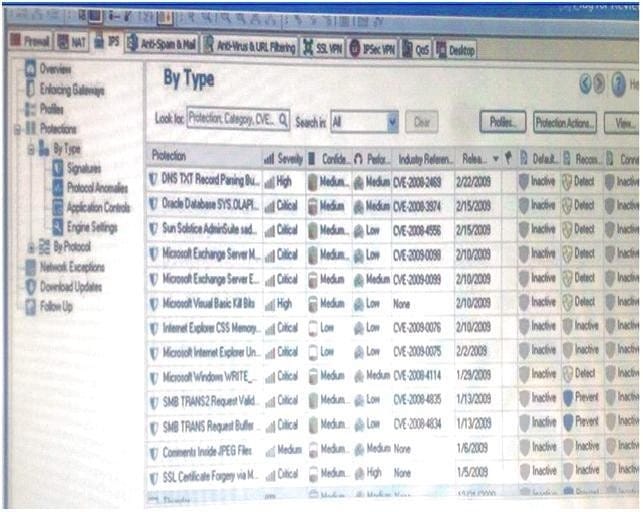
Using the out below, how would Laura change the Default_Protection on Performance Impact Protections classified as low from inactive to prevent until meeting her other criteria?
A. Go to Profiles / Default_Protection and uncheck Do not activate protections with performance impact to medium or above
B. Go to Profiles / Default_Protection and select Do not activate protections with performance impact to low or above
C. Go to Profiles / Default_Protection and select Do not activate protections with performance impact to medium or above
D. Go to Profiles / Default_Protection and uncheck Do not activate protections with performance impact to high or above
-
Question 367:
Based on the following information, which of the statements below is FALSE? A DLP Rule Base has the following conditions: Data Type =Password Protected File Source=My Organization Destination=Outside My Organization Protocol=Any Action=Ask User Exception: Data Type=Any, Source=Research and Development (RandD) Destination=Pratner1.com Protocol=Any All other rules are set to Detect.User Checkis enabled and installed on all client machines.
A. When a user from RandD sends an e-mail with a password protected PDF file as an attachment to xyz@partner1 .com, he will be prompted byUser Check.
B. When a user from Finance sends an e-mail with an encrypted ZIP file as an attachment to. He will be prompted byUser Check.
C. Another rule is added: Source = RandD, Destination = partner1.com, Protocol = Any, Action = Inform. When a user from RandD sends an e-mail with an encrypted ZIP file as an attachment to, he will be prompted byUser Check.
D. When a user from RandD sends an e-mail with an encrypted ZIP file as an attachment to , he will NOT be prompted byUser Check.
-
Question 368:
Rachel is the Security Administrator for a university. The university's FTP servers have old hardware and software. Certain FTP commands cause the FTP servers to malfunction. Upgrading the FTP servers is not an option at this time. Which of the following options will allow Rachel to control which FTP commands pass through the Security Gateway protecting the FTP servers?
A. Global Properties > Security Server > Allowed FTP Commands
B. SmartDefense > Application Intelligence > FTP Security Server
C. Rule Base > Action Field > Properties
D. Web Intelligence > Application Layer > FTP Settings
E. FTP Service Object > Advanced > Blocked FTP Commands
-
Question 369:
How is change approved for implementation in SmartWorkflow?
A. The change is submitted for approval and is automatically installed by the approver once Approve is clicked
B. The change is submitted for approval and is automatically installed by the original submitter the next time he logs in after approval of the 3nge
C. The change is submitted for approval and is manually installed by the original submitter the next time he logs in after approval of the change.
D. The change is submitted for approval and is manually installed by the approver once Approve is clicked
-
Question 370:
What is the best tool to produce a report which represents historical system information?
A. Smart ViewTracker
B. Smart viewMonitor
C. Smart Reporter-Standard Reports
D. Smart Reporter-Express Reports
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.