Exam Details
Exam Code
:156-315.77Exam Name
:Check Point Certified Security ExpertCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-315.77 Questions & Answers
-
Question 191:
Where is the ideal place to deploy your SSL VPN?
A. Deployed in DMZ
B. SSL VPN enabled on the gateway
C. In front of the external interface on the gateway
D. Anywhere
-
Question 192:
Which procedure will create an Internal User?
A. In the Users and Administrators tab, right click Users and click SSL VPN User
B. In the General Properties of the gateway, click the SSL VPN check box. The SSL VPN Blade Wizard will launch and Step 2 will allow adding new users who will be imported from a RADIUS server.
C. From the SSL VPN tab, click Users and Authentication I Internal Users I Users and click New User I Default
D. In the Users and Administrators tab, click User Groups I Clientless-vpn-user and add the SSL VPN user to the Clientless-vpn-user group
-
Question 193:
Which of the following is NOT a supported browser for Management Portal?
A. Internet Explorer
B. Safari
C. Firefox
D. Mozilla
-
Question 194:
You enable Sweep Scan Protection and Host port scan in IPS to determine if a large amount of traffic from a specific internal IP address is a network attack, or a user's system is infected with a worm. Will you get all the information you need from these actions?
A. Yes. IPS will limit the traffic impact from the scans, and identify if the pattern of the traffic matches any known worms.
B. No. These IPS protections will only block the traffic, but it will not provide a detailed analysis of the traffic.
C. No. To verify if this is a worm or an active attack, you must also enable TCP attack defenses.
D. No. The logs and alert can provide some level of information, but determining whether the attack is intentional or a worm, requires further research.
-
Question 195:
What are theSmart ProvisioningPolicy Status indicators?
A. OK, Down, Up, Synchronized
B. OK, Waiting, Out of Sync, Not Installed, Not communicating
C. OK, Unknown, Not Installed, May be out of date
D. OK, Waiting, Unknown, Not Installed, Not Updated, May be out of date
-
Question 196:
The We-Make-Widgets company has purchased twenty UTM-1 Edge appliances for their remote offices. Kim decides the best way to manage those appliances is to useSmart Provisioningand create a profile they can all use. List the order of steps Kim would go through to add the Dallas Edge appliance to the Remote Office profile using the output below.
1.
Enter the name of the profile called "Remote Offices"
2.
Change the provisioning profile to "Remote Offices"
3.
Click File, then select New, then Provisioning Profile
4.
Click on the Devices Tab
5.
Highlight the Dallas Edge appliance, click Edit, then edit Gateway
6.
Click on the Profiles Tab
A. 6, 3, 1, 4, 5, 2
B. 4, 1, 3, 6, 5, 2
C. 6, 1, 3, 4, 5, 2
D. 4, 3, 1, 6, 5, 2
-
Question 197:
When a security administrator logs in toSmart Dashboardand selects Continue without session from the followingwindow,whatkind of access will be granted to him inSmart Dashboard?
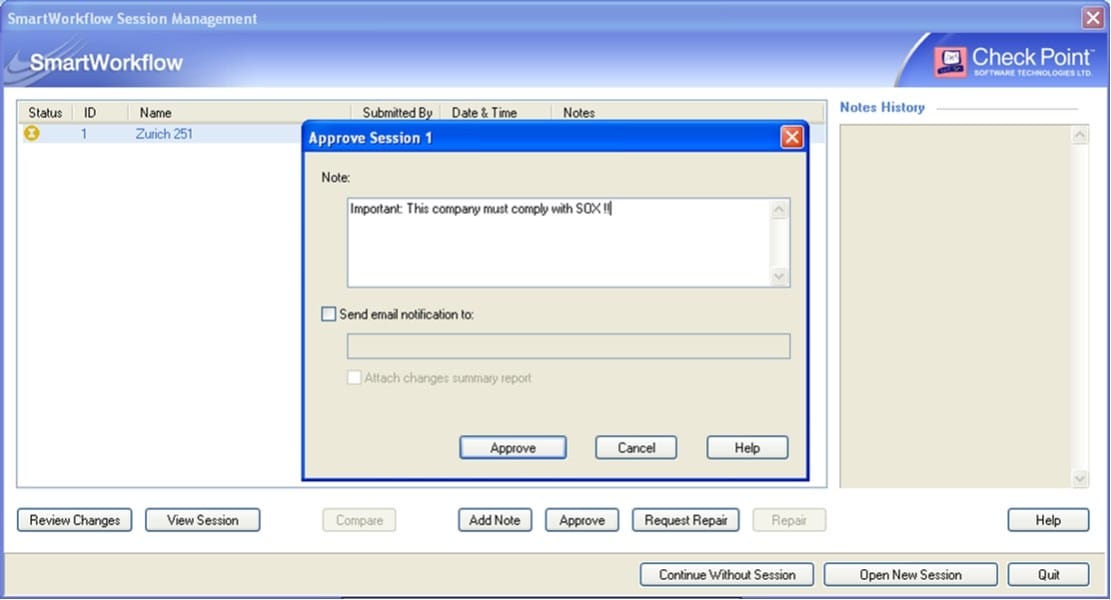
A. He will get read-only access to the policy, network objects and session management.
B. He will get read-only access to the policy and network objects; however, he can still manage the sessions, i.e. Approve, Request Repair etc.
C. A new session will automatically be created with a default session name along with date and time. All changes made by the manager will be saved in this new session.
D. No access will be granted, he will be logged out ofSmart Dashboard.
-
Question 198:
To configure a Security Management Server for an SSL VPN Gateway, you can set up log forwarding from that Gateway. All of the following tasks must be performed to accomplish this, EXCEPT:
A. Defining a remote log server in the "Remote Log Server" box.
B. Establishing SIC between the Security Management Server and the SSL VPN Gateway.
C. Initiating the put key process in order to facilitate Secure Internal Communications (SIC).
D. Providing the Security Management Server's IP address.
-
Question 199:
Can end users be forced to authenticate by using client certificates and username/password credentials?
A. Yes, but by manually changing the parameter :IsPasswordWarning to true in the $FWDIR/conf/objects_5_0.C file, to allow for LDAP password remediation; and through the use of multiple-challenge login pages.
B. No, R71 only supports authentication by client certificates.
C. Yes, by editing the protection-level settings.
D. SSL VPN only supports server certificates.
-
Question 200:
What does it mean when a Security Gateway is labeled Untrusted in theSmart ProvisioningStatus view?
A. SIC has not been established between the Security Gateway and the Security Management.
B. Smart Provisioningis not enabled on the Security Gateway,
C. cpd is not running at the Security Gateway.
D. The Security Gateway is down.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.