Exam Details
Exam Code
:156-215.81Exam Name
:Check Point Certified Security Administrator - R81 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:400 Q&AsLast Updated
:Aug 08, 2025
CheckPoint Checkpoint Certifications 156-215.81 Questions & Answers
-
Question 311:
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
A. Remote Access
B. Cloud IdP (Identity Provider)
C. Active Directory Query
D. RADIUS
-
Question 312:
Which of the following is NOT supported by Bridge Mode Check Point Security Gateway
A. Antivirus
B. Data Loss Prevention
C. NAT
D. Application Control
-
Question 313:
Which software blade enables Access Control policies to accept, drop, or limit web site access based on user, group, and/or machine?
A. Application Control
B. Data Awareness
C. Identity Awareness
D. Threat Emulation
-
Question 314:
What is the main objective when using Application Control?
A. To filter out specific content.
B. To assist the firewall blade with handling traffic.
C. To see what users are doing.
D. Ensure security and privacy of information.
-
Question 315:
Which tool is used to enable ClusterXL?
A. SmartUpdate
B. cpconfig
C. SmartConsole
D. sysconfig
-
Question 316:
To view statistics on detected threats, which Threat Tool would an administrator use?
A. Protections
B. IPS Protections
C. Profiles
D. ThreatWiki
-
Question 317:
Which is a suitable command to check whether Drop Templates are activated or not?
A. fw ctl get int activate_drop_templates
B. fwaccel stat
C. fwaccel stats
D. fw ctl templates -d
-
Question 318:
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings. The following Threat Prevention Profile has been created.
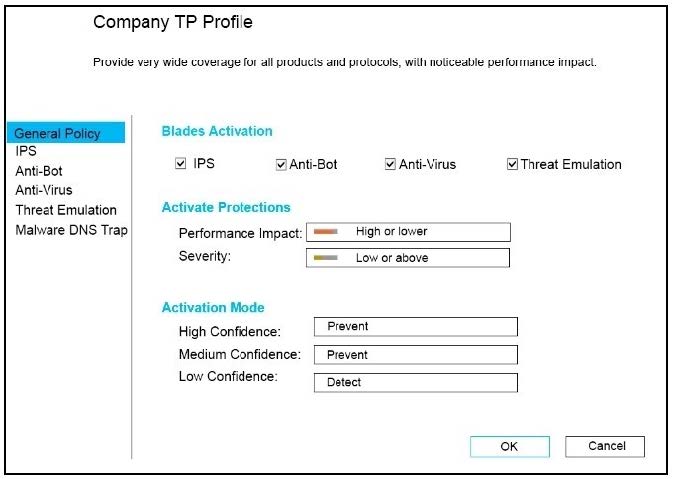
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
A. Set High Confidence to Low and Low Confidence to Inactive.
B. Set the Performance Impact to Medium or lower.
C. The problem is not with the Threat Prevention Profile. Consider adding more memory to the appliance.
D. Set the Performance Impact to Very Low Confidence to Prevent.
-
Question 319:
What is a role of Publishing?
A. The Publish operation sends the modifications made via SmartConsole in the private session and makes them public
B. The Security Management Server installs the updated policy and the entire database on Security Gateways
C. The Security Management Server installs the updated session and the entire Rule Base on Security Gateways
D. Modifies network objects, such as servers, users, services, or IPS profiles, but not the Rule Base
-
Question 320:
Your internal networks 10.1.1.0/24, 10.2.2.0/24 and 192.168.0.0/16 are behind the Internet Security Gateway. Considering that Layer 2 and Layer 3 setup is correct, what are the steps you will need to do in SmartConsole in order to get the connection working?
A. 1. Define an accept rule in Security Policy.2. Define Security Gateway to hide all internal networks behind the gateway's external IP.3. Publish and install the policy.
B. 1. Define an accept rule in Security Policy.2. Define automatic NAT for each network to NAT the networks behind a public IP.3. Publish the policy.
C. 1. Define an accept rule in Security Policy.2. Define automatic NAT for each network to NAT the networks behind a public IP.3. Publish and install the policy.
D. 1. Define an accept rule in Security Policy.2. Define Security Gateway to hide all internal networks behind the gateway's external IP.3. Publish the policy.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.