Exam Details
Exam Code
:156-215.81Exam Name
:Check Point Certified Security Administrator - R81 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:400 Q&AsLast Updated
:Aug 08, 2025
CheckPoint Checkpoint Certifications 156-215.81 Questions & Answers
-
Question 111:
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ______ layer(s) of the TCP/IP model and up to and including the ______ layer.
A. Upper; Application
B. First two; Internet
C. Lower; Application
D. First two; Transport
-
Question 112:
To enforce the Security Policy correctly, a Security Gateway requires:
A. a routing table
B. awareness of the network topology
C. a Demilitarized Zone
D. a Security Policy install
-
Question 113:
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
A. Next Generation Threat Prevention
B. Next Generation Threat Emulation
C. Next Generation Threat Extraction
D. Next Generation Firewall
-
Question 114:
What technologies are used to deny or permit network traffic?
A. Stateful Inspection. Firewall Blade, and URL'Application Blade
B. Packet Filtenng. Stateful Inspection, and Application Layer Firewall
C. Firewall Blade. URL/Application Blade and IPS
D. Stateful Inspection. URL/Application Blade, and Threat Prevention
-
Question 115:
Fill in the blanks: There are ________ types of software containers ________.
A. Three; security management, Security Gateway, and endpoint security
B. Three; Security gateway, endpoint security, and gateway management
C. Two; security management and endpoint security
D. Two; endpoint security and Security Gateway
-
Question 116:
The Online Activation method is available for Check Point manufactured appliances. How does the administrator use the Online Activation method?
A. The SmartLicensing GUI tool must be launched from the SmartConsole for the Online Activation tool to start automatically.
B. No action is required if the firewall has internet access and a DNS server to resolve domain names.
C. Using the Gaia First Time Configuration Wizard, the appliance connects to the Check Point User Center and downloads all necessary licenses and contracts.
D. The cpinfo command must be run on the firewall with the switch -online-license- activation.
-
Question 117:
What protocol is specifically used for clustered environments?
A. Clustered Protocol
B. Synchronized Cluster Protocol
C. Control Cluster Protocol
D. Cluster Control Protocol
-
Question 118:
When configuring Anti-Spoofing, which tracking options can an Administrator select?
A. Log, Alert, None
B. Log, Allow Packets, Email
C. Drop Packet, Alert, None
D. Log, Send SNMP Trap, Email
-
Question 119:
What is the most recommended installation method for Check Point appliances?
A. SmartUpdate installation
B. DVD media created with Check Point ISOMorphic
C. USB media created with Check Point ISOMorphic
D. Cloud based installation
-
Question 120:
You can see the following graphic:
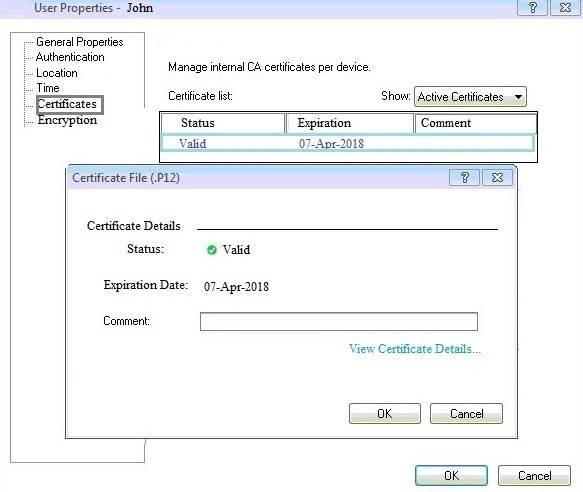
What is presented on it?
A. Properties of personal. p12 certificate file issued for user John.
B. Shared secret properties of John's password.
C. VPN certificate properties of the John's gateway.
D. Expired. p12 certificate properties for user John.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.