Exam Details
Exam Code
:156-215.81.20Exam Name
:Check Point Certified Security Administrator - R81.20 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:677 Q&AsLast Updated
:Jul 27, 2025
CheckPoint Checkpoint Certifications 156-215.81.20 Questions & Answers
-
Question 541:
Fill in the blank: Each cluster has __________ interfaces.
A. Five
B. Two
C. Three
D. Four
-
Question 542:
What are the three essential components of the Check Point Security Management Architecture?
A. SmartConsole, Security Management Server, Security Gateway
B. SmartConsole, SmartUpdate, Security Gateway
C. Security Management Server, Security Gateway, Command Line Interface
D. WebUI, SmartConsole, Security Gateway
-
Question 543:
What are the two types of address translation rules?
A. Translated packet and untranslated packet
B. Untranslated packet and manipulated packet
C. Manipulated packet and original packet
D. Original packet and translated packet
-
Question 544:
You are unable to login to SmartDashboard. You log into the management server and run #cpwd_admin list with the following output:
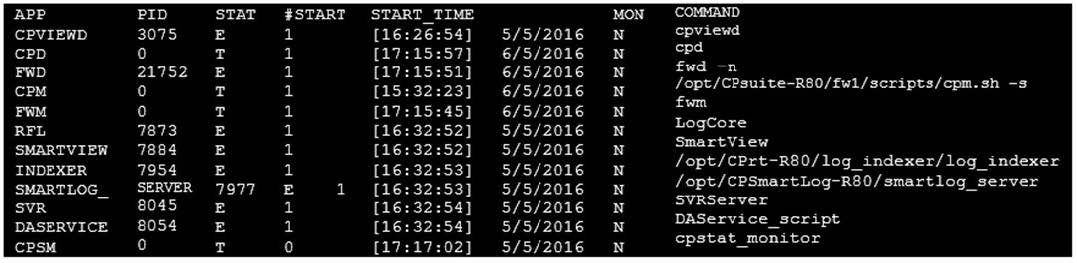
What reason could possibly BEST explain why you are unable to connect to SmartDashboard?
A. CDP is down
B. SVR is down
C. FWM is down
D. CPSM is down
-
Question 545:
What does ExternalZone represent in the presented rule?

A. The Internet.
B. Interfaces that administrator has defined to be part of External Security Zone.
C. External interfaces on all security gateways.
D. External interfaces of specific gateways.
-
Question 546:
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _____________ A. User data base corruption
B. LDAP conflicts
C. Traffic issues
D. Phase two key negotiation
-
Question 547:
What are the two high availability modes?
A. Load Sharing and Legacy
B. Traditional and New
C. Active and Standby
D. New and Legacy
-
Question 548:
Fill in the blank: The R80 feature ________ permits blocking specific IP addresses for a specified time period.
A. Block Port Overflow
B. Local Interface Spoofing
C. Suspicious Activity Monitoring
D. Adaptive Threat Prevention
-
Question 549:
Which Threat Prevention Software Blade provides comprehensive against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
A. Anti-Virus
B. IPS
C. Anti-Spam
D. Anti-bot
-
Question 550:
What is the purpose of Captive Portal?
A. It provides remote access to SmartConsole
B. It manages user permission in SmartConsole
C. It authenticates users, allowing them access to the Internet and corporate resources
D. It authenticates users, allowing them access to the Gaia OS
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81.20 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.