Exam Details
Exam Code
:156-215.81.20Exam Name
:Check Point Certified Security Administrator - R81.20 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:677 Q&AsLast Updated
:Jul 27, 2025
CheckPoint Checkpoint Certifications 156-215.81.20 Questions & Answers
-
Question 511:
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ________ .
A. The license is attached to the wrong Security Gateway
B. The existing license expires
C. The license is upgraded
D. The IP address of the Security Management or Security Gateway has changed
-
Question 512:
What is the default shell for the command line interface?
A. Expert
B. Clish
C. Admin
D. Normal
-
Question 513:
When you upload a package or license to the appropriate repository in SmartUpdate, where is the package or license stored
A. Security Gateway
B. Check Point user center
C. Security Management Server
D. SmartConsole installed device
-
Question 514:
Fill in the blank: The tool _______ generates a R80 Security Gateway configuration report.
A. infoCP
B. infoview
C. cpinfo
D. fw cpinfo
-
Question 515:
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
A. vpn tu
B. vpn ipsec remove -l
C. vpn debug ipsec
D. fw ipsec tu
-
Question 516:
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
A. Security questions
B. Check Point password
C. SecurID
D. RADIUS
-
Question 517:
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
A. Auditor
B. Read Only All
C. Super User
D. Full Access
-
Question 518:
Packages and licenses are loaded from all of these sources EXCEPT
A. Download Center Web site
B. UserUpdate
C. User Center
D. Check Point DVD
-
Question 519:
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
A. INSPECT Engine
B. Stateful Inspection
C. Packet Filtering
D. Application Layer Firewall
-
Question 520:
On the following graphic, you will find layers of policies.
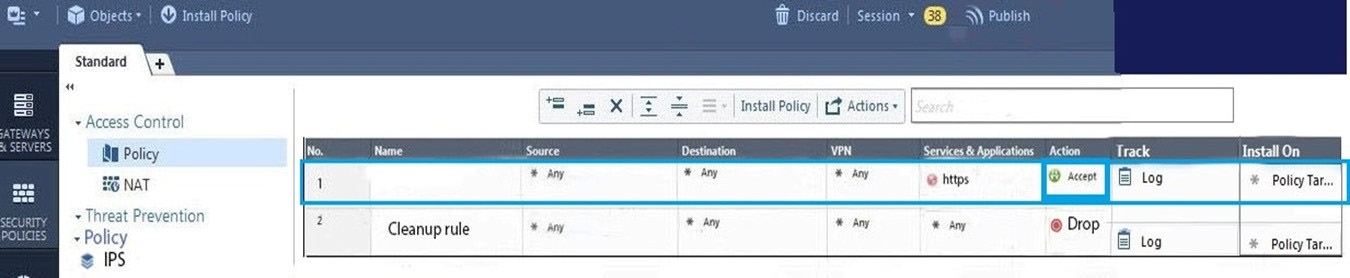
What is a precedence of traffic inspection for the defined polices?
A. A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if implicit Drop Rule drops the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer.
B. A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer
C. A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to Threat Prevention layer and then after accepting the packet it passes to IPS layer.
D. A packet arrives at the gateway, it is checked against the rules in IPS policy layer and then it comes next to the Network policy layer and then after accepting the packet it passes to Threat Prevention layer.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81.20 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.