Exam Details
Exam Code
:156-215.81.20Exam Name
:Check Point Certified Security Administrator - R81.20 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:677 Q&AsLast Updated
:Jul 27, 2025
CheckPoint Checkpoint Certifications 156-215.81.20 Questions & Answers
-
Question 321:
Which of these components does NOT require a Security Gateway R77 license?
A. Security Management Server
B. Check Point Gateway
C. SmartConsole
D. SmartUpdate upgrading/patching
-
Question 322:
What statement is true regarding Visitor Mode?
A. VPN authentication and encrypted traffic are tunneled through port TCP 443.
B. Only ESP traffic is tunneled through port TCP 443.
C. Only Main mode and Quick mode traffic are tunneled on TCP port 443.
D. All VPN traffic is tunneled through UDP port 4500.
-
Question 323:
Mesh and Star are two types of VPN topologies. Which statement below is TRUE about these types of communities?
A. A star community requires Check Point gateways, as it is a Check Point proprietary technology.
B. In a star community, satellite gateways cannot communicate with each other.
C. In a mesh community, member gateways cannot communicate directly with each other.
D. In a mesh community, all members can create a tunnel with any other member.
-
Question 324:
What CLI utility allows an administrator to capture traffic along the firewall inspection chain?
A. show interface (interface) 璫hain
B. tcpdump
C. tcpdump /snoop
D. fw monitor
-
Question 325:
Your bank's distributed R77 installation has Security Gateways up for renewal. Which SmartConsole application will tell you which Security Gateways have licenses that will expire within the next 30 days?
A. SmartView Tracker
B. SmartPortal
C. SmartUpdate
D. SmartDashboard
-
Question 326:
NAT can NOT be configured on which of the following objects?
A. HTTP Logical Server
B. Gateway
C. Address Range
D. Host
-
Question 327:
The fw monitor utility is used to troubleshoot which of the following problems?
A. Phase two key negotiation
B. Address translation
C. Log Consolidation Engine
D. User data base corruption
-
Question 328:
You are the Security Administrator for MegaCorp. In order to see how efficient your firewall Rule Base is, you would like to see how many often the particular rules match. Where can you see it? Give the BEST answer.
A. In the SmartView Tracker, if you activate the column Matching Rate.
B. In SmartReporter, in the section Firewall Blade ?Activity>; Network Activity with information concerning Top Matched Logged Rules.
C. SmartReporter provides this information in the section Firewall Blade ?Security>; Rule Base Analysis with information concerning Top Matched Logged Rules.
D. It is not possible to see it directly. You can open SmartDashboard and select UserDefined in the Track column. Afterwards, you need to create your own program with an external counter.
-
Question 329:
Study the Rule base and Client Authentication Action properties screen.
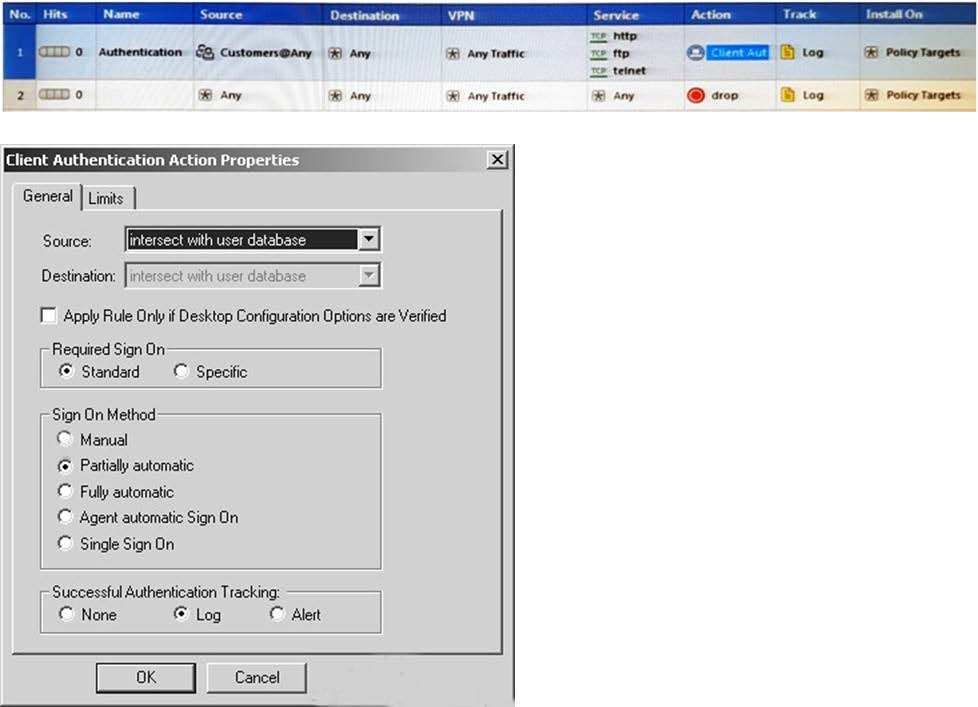
After being authenticated by the Security Gateways, a user starts a HTTP connection to a Web site. What happens when the user tries to FTP to another site using the command line? The:
A. user is prompted for authentication by the Security Gateways again.
B. FTP data connection is dropped after the user is authenticated successfully.
C. user is prompted to authenticate from that FTP site only, and does not need to enter his username and password for Client Authentication
D. FTP connection is dropped by Rule 2.
-
Question 330:
What are the three tabs available in SmartView Tracker?
A. Network and Endpoint, Management, and Active
B. Network, Endpoint, and Active
C. Predefined, All Records, Custom Queries
D. Endpoint, Active, and Custom Queries
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81.20 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.