Exam Details
Exam Code
:156-215.81.20Exam Name
:Check Point Certified Security Administrator - R81.20 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:677 Q&AsLast Updated
:Jul 27, 2025
CheckPoint Checkpoint Certifications 156-215.81.20 Questions & Answers
-
Question 201:
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
A. DLP shared policy
B. Geo policy shared policy
C. Mobile Access software blade
D. HTTPS inspection
-
Question 202:
After trust has been established between the Check Point components, what is TRUE about name and IP-address changes?
A. Security Gateway IP-address cannot be changed without re-establishing the trust
B. The Security Gateway name cannot be changed in command line without re-establishing trust
C. The Security Management Server name cannot be changed in SmartConsole without re-establishing trust
D. The Security Management Server IP-address cannot be changed without re-establishing the trust
-
Question 203:
Which two Identity Awareness commands are used to support identity sharing?
A. Policy Decision Point (PDP) and Policy Enforcement Point (PEP)
B. Policy Enforcement Point (PEP) and Policy Manipulation Point (PMP)
C. Policy Manipulation Point (PMP) and Policy Activation Point (PAP)
D. Policy Activation Point (PAP) and Policy Decision Point (PDP)
-
Question 204:
True or False: In R80, more than one administrator can login to the Security Management Server with write permission at the same time.
A. False, this feature has to be enabled in the Global Properties.
B. True, every administrator works in a session that is independent of the other administrators.
C. True, every administrator works on a different database that is independent of the other administrators.
D. False, only one administrator can login with write permission.
-
Question 205:
Which one of the following is TRUE?
A. Ordered policy is a sub-policy within another policy
B. One policy can be either inline or ordered, but not both
C. Inline layer can be defined as a rule action
D. Pre-R80 Gateways do not support ordered layers
-
Question 206:
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
A. Distributed
B. Bridge Mode
C. Remote
D. Standalone
-
Question 207:
Fill in the blank: An identity server uses a ___________ for user authentication.
A. Shared secret
B. Certificate
C. One-time password
D. Token
-
Question 208:
You can see the following graphic:
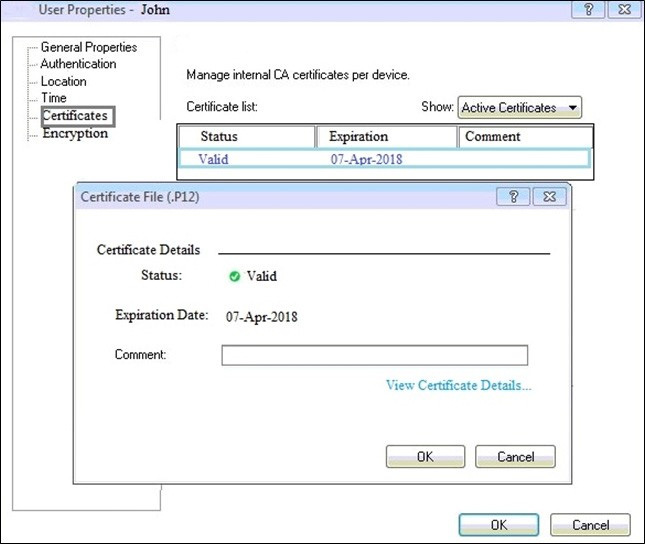
What is presented on it?
A. Properties of personal .p12 certificate file issued for user John.
B. Shared secret properties of John's password.
C. VPN certificate properties of the John's gateway.
D. Expired .p12 certificate properties for user John.
-
Question 209:
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
A. Reflected immediately for all users who are using template.
B. Not reflected for any users unless the local user template is changed.
C. Reflected for all users who are using that template and if the local user template is changed as well.
D. Not reflected for any users who are using that template.
-
Question 210:
Choose what BEST describes the reason why querying logs now is very fast.
A. New Smart-1 appliances double the physical memory install
B. Indexing Engine indexes logs for faster search results
C. SmartConsole now queries results directly from the Security Gateway
D. The amount of logs been store is less than the usual in older versions
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81.20 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.