Exam Details
Exam Code
:156-215.80Exam Name
:Check Point Certified Security Administrator (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:535 Q&AsLast Updated
:Jul 16, 2025
CheckPoint Checkpoint Certifications 156-215.80 Questions & Answers
-
Question 291:
Which of these attributes would be critical for a site-to-site VPN?
A. Scalability to accommodate user groups
B. Centralized management
C. Strong authentication
D. Strong data encryption
-
Question 292:
You have just installed your Gateway and want to analyze the packet size distribution of your traffic with SmartView Monitor.
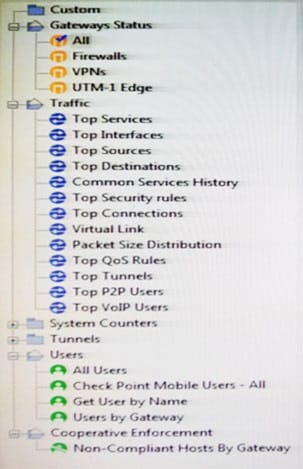
Unfortunately, you get the message:
"There are no machines that contain Firewall Blade and SmartView Monitor".
What should you do to analyze the packet size distribution of your traffic? Give the BEST answer.
A. Purchase the SmartView Monitor license for your Security Management Server.
B. Enable Monitoring on your Security Management Server.
C. Purchase the SmartView Monitor license for your Security Gateway.
D. Enable Monitoring on your Security Gateway.
-
Question 293:
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of your firm's business partners. Which SmartConsole application should you use to confirm your suspicious?
A. SmartDashboard
B. SmartUpdate
C. SmartView Status
D. SmartView Tracker
-
Question 294:
Which of the following uses the same key to decrypt as it does to encrypt?
A. Asymmetric encryption
B. Dynamic encryption
C. Certificate-based encryption
D. Symmetric encryption
-
Question 295:
You are about to test some rule and object changes suggested in an R77 news group. Which backup solution should you use to ensure the easiest restoration of your Security Policy to its previous configuration after testing the changes?
A. Manual copies of the directory $FWDIR/conf
B. upgrade_export command
C. Database Revision Control
D. GAiA backup utilities
-
Question 296:
You are using SmartView Tracker to troubleshoot NAT entries. Which column do you check to view the NAT'd source port if you are using Source NAT?
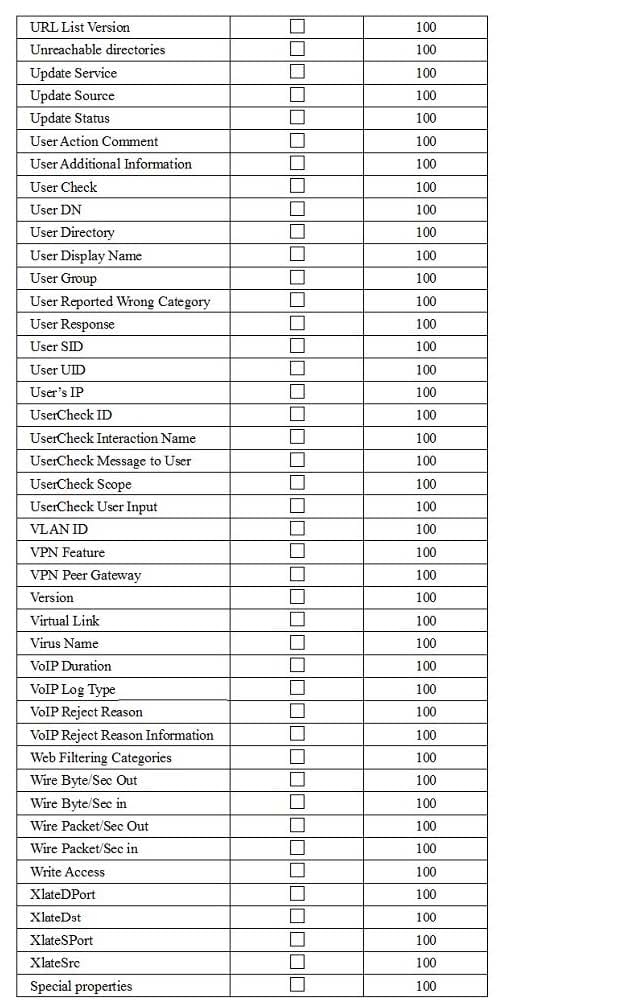
A. XlateDst
B. XlateSPort
C. XlateDPort
D. XlateSrc
-
Question 297:
What happens if the identity of a user is known?
A. If the user credentials do not match an Access Role, the traffic is automatically dropped.
B. If the user credentials do not match an Access Role, the system displays a sandbox.
C. If the user credentials do not match an Access Role, the gateway moves onto the next rule.
D. If the user credentials do not match an Access Role, the system displays the Captive Portal.
-
Question 298:
Your company enforces a strict change control policy. Which of the following would be MOST effective for quickly dropping an attacker's specific active connection?
A. Change the Rule Base and install the Policy to all Security Gateways
B. Block Intruder feature of SmartView Tracker
C. Intrusion Detection System (IDS) Policy install
D. SAM ?Suspicious Activity Rules feature of SmartView Monitor
-
Question 299:
What port is used for communication to the User Center with SmartUpdate?
A. CPMI 200
B. TCP 8080
C. HTTP 80
D. HTTPS 443
-
Question 300:
As you review this Security Policy, what changes could you make to accommodate Rule 4?
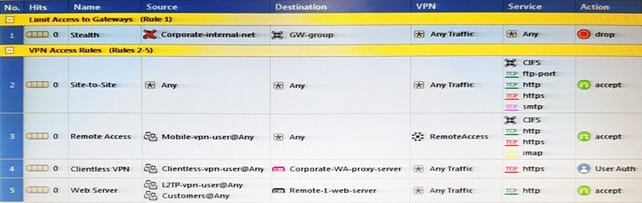
A. Remove the service HTTP from the column Service in Rule 4.
B. Modify the column VPN in Rule 2 to limit access to specific traffic.
C. Nothing at all
D. Modify the columns Source or Destination in Rule 4
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.