Exam Details
Exam Code
:156-215.80Exam Name
:Check Point Certified Security Administrator (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:535 Q&AsLast Updated
:Jul 07, 2025
CheckPoint Checkpoint Certifications 156-215.80 Questions & Answers
-
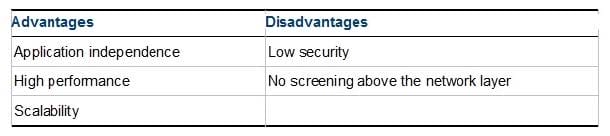
Question 121:
What is NOT an advantage of Packet Filtering?
A. Low Security and No Screening above Network Layer
B. Application Independence
C. High Performance
D. Scalability
-
Question 122:
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server (Security Management Server)?
A. Display policies and logs on the administrator's workstation.
B. Verify and compile Security Policies.
C. Processing and sending alerts such as SNMP traps and email notifications.
D. Store firewall logs to hard drive storage.
-
Question 123:
Web Control Layer has been set up using the settings in the following dialogue:
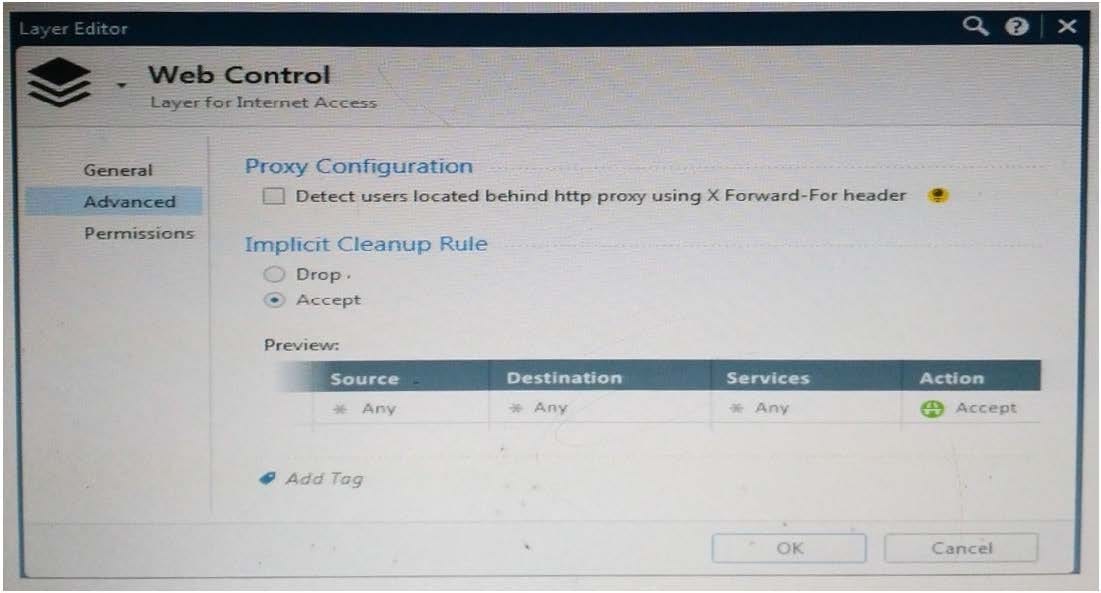
Consider the following policy and select the BEST answer.
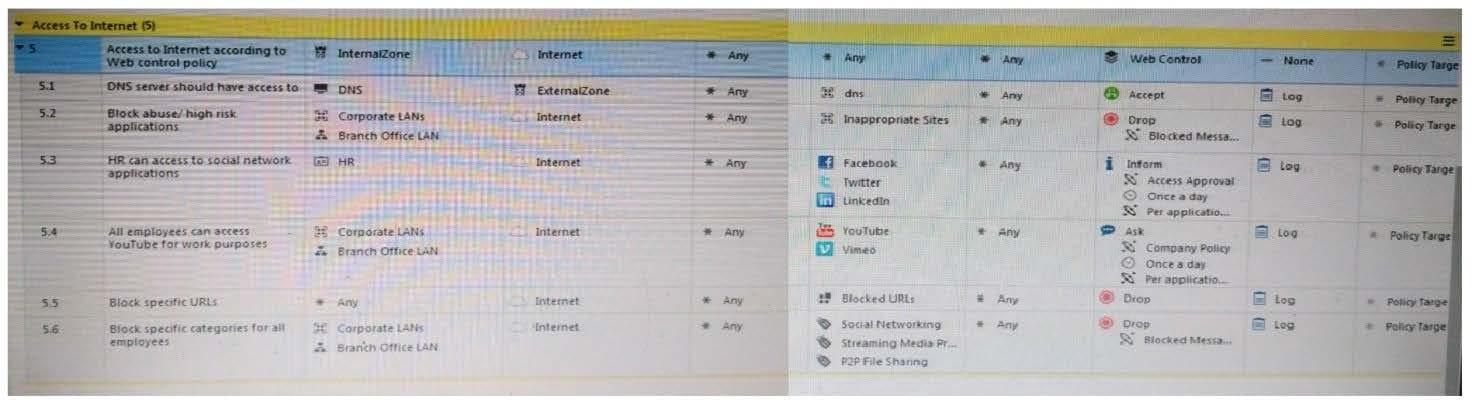
A. Traffic that does not match any rule in the subpolicy is dropped.
B. All employees can access only Youtube and Vimeo.
C. Access to Youtube and Vimeo is allowed only once a day.
D. Anyone from internal network can access the internet, expect the traffic defined in drop rules 5.2, 5.5 and 5.6.
-
Question 124:
When attempting to start a VPN tunnel, in the logs the error 'no proposal chosen' is seen numerous times. No other VPN-related log entries are present. Which phase of the VPN negotiations has failed?
A. IKE Phase 1
B. IPSEC Phase 2
C. IPSEC Phase 1
D. IKE Phase 2
-
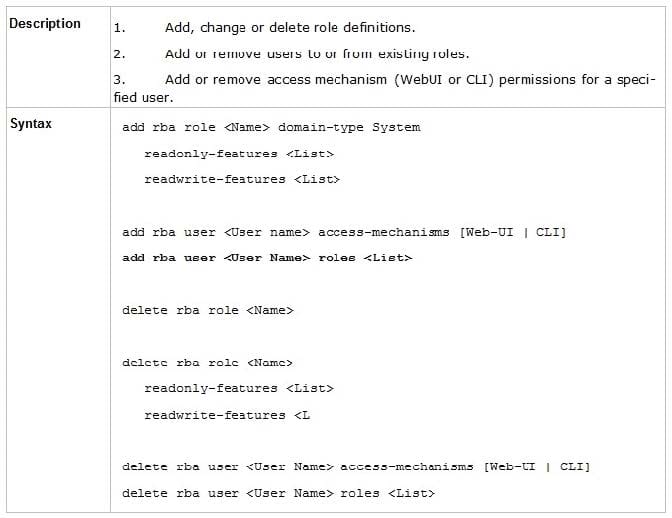
Question 125:
Which command is used to add users to or from existing roles?
A. Add rba user
roles B. Add rba user
C. Add user
roles D. Add user
-
Question 126:
View the rule below. What does the lock-symbol in the left column mean? Select the BEST answer.

A. The current administrator has read-only permissions to Threat Prevention Policy.
B. Another user has locked the rule for editing.
C. Configuration lock is present. Click the lock symbol to gain read-write access.
D. The current administrator is logged in as read-only because someone else is editing the policy.
-
Question 127:
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain. Why does it not detect the windows domain?
A. Security Gateways is not part of the Domain
B. SmartConsole machine is not part of the domain
C. SMS is not part of the domain
D. Identity Awareness is not enabled on Global properties
-
Question 128:
What is the purpose of Captive Portal?
A. It provides remote access to SmartConsole
B. It manages user permission in SmartConsole
C. It authenticates users, allowing them access to the Internet and corporate resources
D. It authenticates users, allowing them access to the Gaia OS
-
Question 129:
Which Threat Prevention Software Blade provides comprehensive against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
A. Anti-Virus
B. IPS
C. Anti-Spam
D. Anti-bot
-
Question 130:
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _____________
A. User data base corruption
B. LDAP conflicts
C. Traffic issues
D. Phase two key negotiation
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.