Exam Details
Exam Code
:156-215.77Exam Name
:Check Point Certified Security AdministratorCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-215.77 Questions & Answers
-
Question 311:
By default, when you click File > Switch Active File in SmartView Tracker, the Security Management Server:
A. Saves the current log file, names the log file by date and time, and starts a new log file.
B. Purges the current log file, and starts a new log file.
C. Prompts you to enter a filename, and then saves the log file.
D. Purges the current log file, and prompts you for the new log's mode.
-
Question 312:
Your Security Management Server fails and does not reboot. One of your remote Security Gateways managed by the Security Management Server reboots. What occurs with the remote Gateway after reboot?
A. Since the Security Management Server is not available, the remote Gateway cannot fetch the Security Policy. Therefore, all traffic is allowed through the Gateway.
B. Since the Security Management Server is not available, the remote Gateway cannot fetch the Security Policy. Therefore, no traffic is allowed through the Gateway.
C. The remote Gateway fetches the last installed Security Policy locally and passes traffic normally. The Gateway will log locally, since the Security Management Server is not available.
D. Since the Security Management Server is not available, the remote Gateway uses the local Security Policy, but does not log traffic.
-
Question 313:
You enable Hide NAT on the network object, 10.1.1.0 behind the Security Gateway's external interface. You browse to the Google Website from host, 10.1.1.10 successfully. You enable a log on the rule that allows 10.1.1.0 to exit the network. How many log entries do you see for that connection in SmartView Tracker?
A. Two, one for outbound, one for inbound
B. Only one, outbound
C. Two, both outbound, one for the real IP connection and one for the NAT IP connection
D. Only one, inbound
-
Question 314:
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?

As expert user, issue these commands:
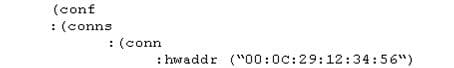
A. Edit the file /etc/sysconfig/netconf.C and put the new MAC address in the field
B. As expert user, issue the command:
C. # IP link set eth0 addr 00:0C:29:12:34:56
D. Open the WebUI, select Network > Connections > eth0. Place the new MAC address in the field Physical Address, and press Apply to save the settings.
-
Question 315:
The customer has a small Check Point installation, which includes one GAiA server working as the SmartConsole, and a second server running Windows 2008 as both Security Management Server and Security Gateway. This is an example of a(n):
A. Distributed Installation
B. Hybrid Installation
C. Unsupported configuration
D. Stand-Alone Installation
-
Question 316:
You have configured Automatic Static NAT on an internal host-node object. You clear the box Translate destination on client site from Global Properties > NAT. Assuming all other NAT settings in Global Properties are selected, what else must be configured so that a host on the Internet can initiate an inbound connection to this host?
A. No extra configuration is needed.
B. A proxy ARP entry, to ensure packets destined for the public IP address will reach the Security Gateway's external interface.
C. The NAT IP address must be added to the external Gateway interface anti-spoofing group.
D. A static route, to ensure packets destined for the public NAT IP address will reach the Gateway's internal interface.
-
Question 317:
You have detected a possible intruder listed in SmartView Tracker's active pane. What is the fastest method to block this intruder from accessing your network indefinitely?
A. Modify the Rule Base to drop these connections from the network.
B. In SmartView Tracker, select Tools > Block Intruder.
C. In SmartView Monitor, select Tools > Suspicious Activity Rules.
D. In SmartDashboard, select IPS > Network Security > Denial of Service.
-
Question 318:
Which Check Point address translation method allows an administrator to use fewer ISP- assigned IP addresses than the number of internal hosts requiring Internet connectivity?
A. Hide
B. Static Destination
C. Static Source
D. Dynamic Destination
-
Question 319:
Your internal network is configured to be 10.1.1.0/24. This network is behind your perimeter R77 Gateway, which connects to your ISP provider. How do you configure the Gateway to allow this network to go out to the Internet?
A. Use Hide NAT for network 10.1.1.0/24 behind the external IP address of your perimeter Gateway.
B. Use Hide NAT for network 10.1.1.0/24 behind the internal interface of your perimeter Gateway.
C. Use automatic Static NAT for network 10.1.1.0/24.
D. Do nothing, as long as 10.1.1.0 network has the correct default Gateway.
-
Question 320:
Your bank's distributed R77 installation has Security Gateways up for renewal. Which SmartConsole application will tell you which Security Gateways have licenses that will expire within the next 30 days?
A. SmartView Tracker
B. SmartPortal
C. SmartUpdate
D. SmartDashboard
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.